The Quaestor - Volume 12, Issue 1
Breadcrumb
- RIT/
- Finance and Administration/
- Institute Audit, Compliance & Advisement/
- The Quaestor - Volume 12, Issue 1
Who Audits the Auditors?
Contributed by: Nancy A. Nasca, Manager, Institute Audit, Compliance & Advisement, naniaca@rit.edu
Have you ever wondered who audits the auditors? At IACA, we strive to adhere to the highest level of compliance with the standards applicable to the practice of internal auditing, the Institute of Internal Auditors’ (IIA’s) International Standards for the Professional Practice of Internal Auditing (Standards). The Standards are categorized into two main categories, Attribute and Performance Standards.
Attribute Standards address the key characteristics required for a quality internal audit function such as authority, independence, objectivity, competence, professional development, quality assurance, and improvement. Performance Standards provide quality criteria against which the performance of internal audit services can be measured in areas such as engagement planning, objectives, scope, documentation, and reporting.
Attribute Standard 1312 – External Assessments requires an appraisal be conducted at least once every five years by an outside independent assessor or assessment team to evaluate an internal audit activity’s conformance with The IIA’s Definition of Internal Auditing, Code of Ethics, and Standards. This external assessment can be in the form of a full external assessment, or a self-assessment with independent external validation.
Similar to the Middle States Accreditation process, IACA utilizes a self-assessment with independent external validation which involves the use of a qualified, independent external assessment team of two validators to conduct an independent validation of the internal self-assessment. Independent external assessors must be well versed in successful internal audit practices.
A self-assessment with independent external validation includes a comprehensive and fully documented self-assessment process that requires the chief audit executive (CAE) to oversee the efforts of an internal assessment team that completes planning documentation, performs assessment work programs, evaluates conformance with The IIA’s mandatory guidance, and produces a report summarizing assessment results.
The independent assessment team validates the work of the internal assessment team through review of assessment planning documentation, re-performing a sample of assessment work program steps, conducting interviews with key stakeholders (trustees, executive leadership, operating management, and internal audit staff), and assessing the conformance conclusions reported by the internal assessment team. The external assessment team will conclude on whether or not IACA has achieved conformance with the Standards. The Standards require IACA to report the results of the external assessment to senior management and the Audit Committee of the Board of Trustees.
IACA’s next assessment, will occur in April 2017, will be the third one we have completed (previous assessments were performed in 2012 and 2007). In both of our prior assessments, IACA was found to be in conformance with the Standards. Not all of our internal audit peers at other higher education institutions complete these assessments, so we take great pride in knowing we are operating at the highest levels of standards and practices in our profession.
We are looking forward to our “audit!”
Reference
International Professional Practices Framework (IPPF), by the Institute of Internal Auditors.
Inform RIT
Contributed by: Ben Woelk, Program Manager, RIT Information Security Office, infosec@rit.edu
Inform RIT is a recurring column provided by the RIT Information Security Office. The column highlights current issues and initiatives that impact the RIT community. In this issue, we’ll talk about the importance of backups. A special thank you to Andrew McKenzie, Information Security Associate for drafting the original article.
WHAT IS A DATA BACKUP?
Backing up data is the process of copying files and folders to a separate secure location for the purpose of restoring them in case of data loss. Losing data is harmful to both individuals and companies as it may result in months’ or years’ worth of work if the information is destroyed and otherwise unrecoverable. Within the last few years, data loss has become a huge issue because of the rise of ransomware, a dangerous malware capable of encrypting a user’s data so that the data cannot be recovered unless a “ransom” is paid to the attacker.
WHY SHOULD I BACK UP MY COMPUTER?
Backing up a computer allows the recovery of data that has been lost due to an incident such as a ransomware attack or even physical destruction. Backups are fast, simple, and relatively low cost making it easy for everyone to do it on a regular basis. The amount of time put into backing up a system is well worth the cost of recovering files from data loss or paying a ransom.
WHAT ARE SOME WAYS TO LOSE DATA?
- Ransomware is a malicious attack that is responsible for encrypting a user’s files. The files cannot be recovered unless a fine is payed to the attacker. Backing up your data will make it possible to recover your encrypted files after restoring your system to factory settings. Read more about ransomware at http://www.rit.edu/security/content/ransomware-0.
- Physical destruction is a common cause of data loss...even if your device is destroyed, your data will be safe as long as you backed up your files.
- Theft can also lead to data loss. This is the result of when someone steals your laptop, tablet, or phone and you no longer have access to your data.
- Hard drive failure occurs when your system’s hard drive crashes/dies and fails to provide the user with their data. This can result from worn out parts and internal damage. The average duration of a hard drive is 5 years.
HOW DO I BACK UP MY DATA AT HOME?
There are several different methods to back up your data. Choose one that feels most convenient to you.
- An external hard drive is an easy-to-use, cost effective option limited only by the amount of data it can store. An external hard drive plugs into your computer so that you copy over any important files that you want to back up directly to the hard drive. (Do not leave it plugged into the computer after backing up to it because it could also be encrypted by the same ransomware that encrypted your files on your internal hard drive.) Keep your hard drive in a place that you will remember and is safe from physical threat, such as a locked drawer near your computer.
- The cloud is a more recent method of backing up data that is free for a limited amount of data. Popular cloud software includes Google Drive and Dropbox. This method is also convenient because it is not a physical device, but an application that can be accessed from any of your devices. Note: if you are a student of RIT, you automatically have access to a Google Drive account that stores an unlimited amount of data.
- A Network Attached Storage device shares features from both an external hard drive and the cloud. It is a device that connects to your network and stores your data without having to plug it into your computer. You can also configure the settings to do automatic backups.
- Time Machine for Mac users is designed to be simple and convenient for personal automatic backups. This program requires an external hard drive as a source for the backups. The Time Machine application runs with a simple user interface designed by Apple making it fast and easy to restore any lost data.
WHAT IF I AM AN EMPLOYEE OF RIT?
Backup options vary at RIT. Check with ITS or your department to determine which method of backup is appropriate for your RIT device. One common method of backing up data on RIT-owned Windows desktop computers within the F&A department is the “FAST User Backup” application that backs up all files to the “share” drive with a simple two-click system. We recommend users save their RIT work on a network share rather than storing all of your data locally. This adds an extra layer of security to your data due to your backups being stored in more than one place: locally and on the share.
HOW OFTEN SHOULD I CONDUCT A DATA BACKUP?
We recommend backing up at a minimum of once a month. How often you back up your data depends on the type of work that you are doing and at what rate. How much data can you afford to lose?
IMPORTANT NOTICE ON BACKUPS
Backing up your files is only one part of making sure that your data is safe. Restoring that data is equally important. Confirm that your backups are working and your data is safe by conducting a restore.
Whether you are using an external hard drive, cloud drive, or a network attached storage device, you should attempt to restore your backups to assure your safety for when the time comes to act.
Guest Author Article: Controller’s Office
Simplifying Signature Delegation and HR/Financial Transactions Approval
Contributed by: Milagros Concepcion, Assistant Controller, Controller’s Office, mxlcto@rit.edu
For the good portion of a year, a team of colleagues from Human Resources, the Controller’s Office and Information Technology Services collaborated on the design of a simplified signature delegation process in compliance with the University’s Signature Authority Policy. The team also worked with stakeholders across campus on the development of a new online approval routing process for HR and financial transactions. Using existing Oracle functionality, Approval Management Engine (AME) Workflow, the re-designed process is paperless, highly streamlined, transparent, easier to maintain, and flexible while enforcing compliance requirements.
Signature Delegation and Approval Limit Amounts (ALA):
- Budget heads can delegate online signatory authority by giving direct reports approval limit amounts (ALA) through the Oracle Responsibility: RIT Approval Limit Delegation.
- Standard list of values are available for supervisors to choose from when delegating HR and financial ALA.
- A direct supervisor’s delegation is routed and approved online by a management level above the supervisor based on the HR organizational chart.
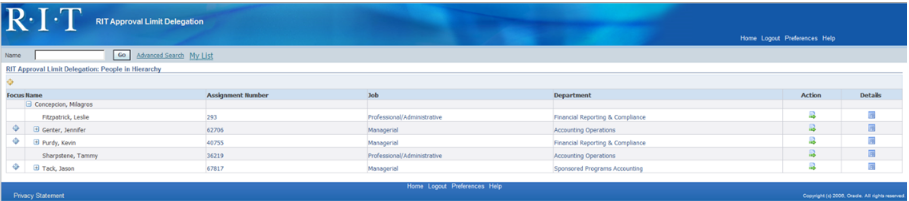
Transaction Approval Routing:
- The new process electronically routes HR supplemental pay, iExpenses, employee reimbursements, online invoice payment forms, requisitions, and invoice loaders.
- AME Workflow is consistent for HR and financial transactions while allowing the ALA to differ.
- Departments can designate a different reviewer and 1st approver for HR and financial transactions.
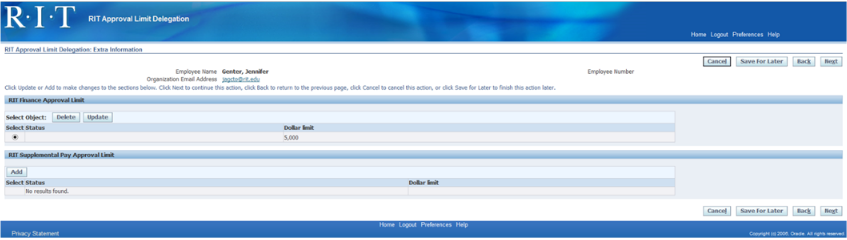
Reviewer:
- Field can be null if the department does not need a transaction reviewer.
- The first employee to review the transaction after it is prepared.
- When the reviewer “approves” the transition, it is forwarded to the 1st approver; if rejected, returns to the preparer for correction.
1st Approver:
- Employee with the lowest Approval Limit Amount (ALA) for a department.
- Determines the supervisory branch the approval will follow.
- Approves transaction if sufficient ALA, otherwise transaction routes to 1st approver's supervisor based on HR supervisory chart and continues until transaction amount is satisfied.
- If also recipient (payee), transaction routes to 1st Approver's supervisor.
Additional Controls:
- Creator or employee in the transaction can't be the final approver.
- Final approver cannot report to the employee in the transaction.
- If creator or employee is also the vacation delegatee of an approver, that approver is skipped.
- Principal investigator must approve all transactions charged to his/her grants.
The Workflow – as easy as 1, 2, 3
- Transactions route first to the employee in the Reviewer field for a department.
- The Reviewer approves the transaction, if the field is blank, the approval request routes to the 1st Approver.
- The 1st approver can approve, or reject the transaction. If the transaction amount is higher than the 1st Approver’s ALA, it routes to the 1st Approver’s supervisor and up the HR supervisory hierarchy until someone with a sufficient ALA can approve it in full.
- The team is currently working on the next and final phase of the project to enable the online re-certifications for approval limit amounts and departmental reviewers and 1st Approvers scheduled to go live October 2017.
Personal Note:
"I am thankful for the opportunity to work side-by-side with colleagues who are committed to the university and its diverse group of stakeholders. We met in-person with those responsible for the approval of HR and financial transactions, explained the functionality, listened to their feedback, made changes/modifications, and went through specific examples. Throughout this process – one principle bound us together, doing “what is best for our customers”.
Committee of Sponsoring Organizations of the Treadway Commission (COSO) Corner
Contributed by: Nancy A. Nasca, Manager, Institute Audit, Compliance & Advisement, naniaca@rit.edu
As explained in previous editions of the Quaestor Quarterly, the COSO Framework (an internationally recognized standard with which the adequacy and effectiveness of an organization’s internal controls are evaluated) was updated in May 2013 to further define the principles underlying the five components of internal control (Control Environment, Risk Assessment, Control Activities, Information and Communication, and Monitoring). According to the Framework, these principles are fundamental concepts that must be present and functioning in order to achieve an effective system of internal control.
In addition, the Framework includes points of focus or characteristics that are examples of behaviors or processes that would be expected to be in place to demonstrate that the related principle is in fact present and functioning. This edition of the COSO Corner will summarize the tenth COSO principle which is the first principle related to the Control Activities component of the COSO Framework, as well as the related points of focus.
Principle 10 – The university selects and develops control activities that contribute to the mitigation of risks to the achievement of objectives to acceptable levels. When designing and implementing control activities, management should consider:
- Alignment with Risk Assessment – Control activities should be in alignment with the assessed level of risk and management’s desired risk response. If management chooses to reduce the likelihood and impact of a risk by implementing control activities, these procedures should be commensurate with the associated risk (i.e., consideration of cost/benefit).
- Implementation of a Mix of Control Activities – Control activities should include a range and variety of controls and a balance of approaches to mitigate risks, including both manual and automated controls, and preventative (e.g., designed to avoid an unintended event or result at the time of initial occurrence) and detective controls (e.g., designed to discover an unintended event or result after the initial processing has occurred but before the ultimate objective has concluded).
- Control Activities at Different Levels of the University – The university should design and implement a mix of control activities that operate both at the transaction-processing level as well as those that operate more broadly and that typically take place at higher levels in the organization (i.e., management oversight and monitoring controls).
- Segregation of Duties – When designing and implementing control activities, management should consider whether responsibilities are divided or segregated among different people to reduce the risk of error or inappropriate or fraudulent actions. Where such segregation is not practical, management should design and implement compensating control activities (i.e., management oversight and monitoring controls).
To learn more about how you can mitigate business risks by establishing and maintaining effective business practices and control activities, register for the IACA training session, “Internal Controls and Fraud in the Workplace,” which is offered quarterly through RIT’s Center for Professional Development.
Reference
Committee of Sponsoring Organizations of the Treadway Commission (May 2013). “Internal Control – Integrated Framework – Framework and Appendices”
Additional Information by IACA
Watch IACA’s Monday Minute video series here!
Our video series focuses on opportunities for improving internal controls and increasing awareness of various university processes, policies, and protocols. If you have questions, feel free to contact anyone in the IACA office using information on our webpage.
Just to name a few, past topics include: Travel Policy changes, FERPA Regulations, RIT’s Ethics & Compliance Hotline, Records Management Policy, Risk Assessment, and many others.
What about ethics in the workplace?
Learn about the RIT Ethics and Compliance Hotline
IACA Team
Learn more about your IACA team.