The Quaestor - Volume 13, Issue 1
Breadcrumb
- RIT/
- Finance and Administration/
- Institute Audit, Compliance & Advisement/
- The Quaestor - Volume 13, Issue 1
Stewardship
Contributed by: Patrick M. Didas, Assistant Vice President, Institute Audit, Compliance & Advisement, pmdiaca@rit.edu
Stewardship is a term that we hear often in a variety of applications and one that is used frequently in mission statements. So, what is stewardship and how does one go about being a good steward?
According to Merriam-Webster’s Dictionary, stewardship is defined as “the conducting, supervising, or managing of something; especially: the careful and responsible management of something entrusted to one's care.” The key terms in the definition are “careful,” “responsible,” and “entrusted;” it’s these terms that truly sets the standard for good stewardship apart from the simple management of something, which can at times be less than optimal.
Most of us likely agree that carefully and responsibly managing university resources in one’s area of responsibility is an expectation. Stewards act as fiduciaries – individuals who have an obligation to act for another, requiring trust, good faith, and honesty. As employees of RIT, we are all stewards - and, therefore, fiduciaries - of RIT’s resources. As such, our daily activities should always be in the best interest of the university. Sometimes, however, there may be temptations to circumvent the “rules” or policies that appear cumbersome. This temptation must be resisted as RIT’s rules and policies exist for a reason; they help to ensure that RIT remains compliant with laws & regulations, assets are secure, and financial information is reliable. With that said, however, it is always fair to challenge why things are done the way they are; this fosters process improvement and helps to ensure that operations are as efficient and effective as possible. If you ever have a question on how you might conduct activities within your area of responsibility more effectively or efficiently, while still employing good stewardship tendencies, contact us and we can provide some feedback on your ideas.
In IACA’s CPD training session, Internal Controls and Fraud in the Workplace, we often mention that a good litmus test for the responsible stewardship of RIT’s resources is to consider the following: would you feel comfortable approaching a student on the Quarter Mile and asking “guess what my department just purchased with some of your tuition dollars?” If contemplating having that discussion makes you feel uncomfortable, then perhaps better stewardship should be exercised in managing those resources; responsible management includes ensuring resources are used for necessary, RIT mission-related activities. And remember these few comments relative to stewardship:
- You set the tone in your area of responsibility.
- That tone should be one of ethical behavior and good stewardship.
- A good steward ensures that university resources are appropriately used to further the university’s mission.
- Self-monitoring can help ensure good stewardship.
- All RIT employees are stewards of RIT resources.
- Internal audits or management-requested advisory engagements that IACA performs help ensure that internal control processes support responsible stewardship and are compliant with policies and regulations. We are here to help you!
Inform RIT
Contributed by: Ben Woelk, Program Manager, RIT Information Security Office, infosec@rit.edu
Inform RIT is a recurring column provided by the RIT Information Security Office. The column highlights current issues and initiatives that impact the RIT community. In this issue, we’ll talk about our new awareness tools to fight phishing attacks.
Although our spam and phishing defenses have improved greatly, thanks to the efforts of the ITS mail team and our Cisco Ironport email appliance, phishing remains one of our greatest threats. Why? Because phishing is low- risk for the attacker and is an effective way to gather usernames and passwords across the world.
We’ve introduced two new security awareness tools to defend against phishing.
RID—Report, Inspect, Delete
You’ve probably noticed that all of our messaging around phishing now includes the acronym RID. We’ve introduced the RID acronym to help you remember what to do when you encounter a suspicious email. (A suspicious email includes any that provides a link for you to verify your password or that includes an unexpected attachment.)
REPORT any phishing attempts to: spam@rit.edu and infosec@rit.edu
INSPECT your computer if you clicked on a suspicious link by running a virus scan. Change your password if you provided it.
DELETE any phishing attempts.
RIT PhishBowl
If you’ve been to our website lately, you may have noticed the RIT PhishBowl. Following the lead of other universities, notably Brown University and Princeton University, we’ve created a place to share phishes that you’ve reported to us.

WELCOME TO THE RIT PHISHBOWL, YOUR SOURCE FOR THE LATEST PHISHING ATTEMPTS REPORTED AT RIT
How do I use the RIT PhishBowl?
If you receive a suspicious email, visit the RIT PhishBowl and scan the list of recent phishing alerts. If the email is posted, there's no need to report it. Simply delete the email and you're done.
If the suspicious email is not posted to the RIT PhishBowl, report the phish:
- Open a new mail note
- Drag the phishing attempt into the new mail note
- Send the mail note to spam@rit.edu and infosec@rit.edu.
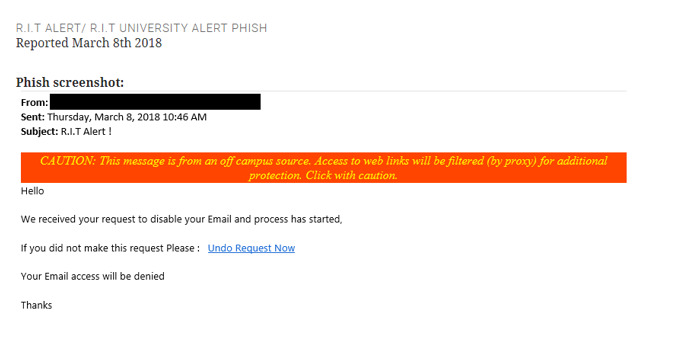
Phish Example from the RIT PhishBowl:
Clicking on the example, you’ll see a screenshot of the phish that was reported.
What’s Next
We’re working on an initiative to create an engaging security awareness campaign at RIT. We’re finalizing the details now. Watch for upcoming communications.
Any questions? Please drop us a note!
Sign up for our DSD101 course, Introduction to Digital Self Defense through CPD.
Committee of Sponsoring Organizations of the Treadway Commission (COSO) Corner
Contributed by: Nancy A. Nasca, Manager, Institute Audit, Compliance & Advisement, naniaca@rit.edu
As explained in previous editions of the Quaestor Quarterly, the COSO Framework (an internationally recognized standard with which the adequacy and effectiveness of an organization’s internal controls are evaluated) was updated in May 2013 to further define the principles underlying the five components of internal control (Control Environment, Risk Assessment, Control Activities, Information and Communication, and Monitoring). According to the Framework, these principles are fundamental concepts that must be present and functioning in order to achieve an effective system of internal control.
In addition, the Framework includes points of focus or characteristics that are examples of behaviors or processes that would be expected to be in place to demonstrate that the related principle is in fact present and functioning. This edition of the COSO Corner will summarize the thirteenth COSO principle, which is the first principle related to the Information and Communication component of the COSO Framework, as well as the related points of focus.
Principle 13 – The university obtains, generates, and uses relevant, quality information to support the functioning of internal control. Important characteristics relating to this principle include:
- The Identification of Information Requirements – Information about RIT’s objectives is gathered from the Board of Trustees and senior management and summarized in a way that promotes employees’ understanding of the university’s key objectives and their role in the achievement of those objectives.
- Capturing Internal and External Sources of Information – Management considers a comprehensive scope of potential events, activities, and data sources available internally and from reliable external sources, and selects those most relevant and useful to the university’s current structure and objectives.
- Processing Relevant Data in Information – Large volumes of data are processed from internal and external sources into meaningful, actionable information needed to meet defined business requirements.
- Maintaining Quality Throughout Processing – The ability to generate quality information (i.e., timely, current, accurate, complete, accessible, protected, verifiable) is critical to supporting sound management decisions.
- The Consideration of Costs and Benefits – The nature, quantity, and precision of information communicated are commensurate with and supportive of the achievement of objectives.
RIT management has established a Data Governance Policy to help the university to manage data along with security, access to, and usage of it. In addition, guidelines are in the process of being developed to facilitate the implementation of a university-wide data governance framework.
Reference
Committee of Sponsoring Organizations of the Treadway Commission (May 2013). “Internal Control – Integrated Framework – Framework and Appendices”
Additional Information by IACA
Watch IACA’s Monday Minute video series here!
Our video series focuses on opportunities for improving internal controls and increasing awareness of various university processes, policies, and protocols. If you have questions, feel free to contact anyone in the IACA office using information on our webpage.
Just to name a few, past topics include: Travel Policy changes, FERPA Regulations, RIT’s Ethics & Compliance Hotline, Records Management Policy, Risk Assessment, and many others.
What about ethics in the workplace?
Learn about the RIT Ethics and Compliance Hotline
IACA Team
Learn more about your IACA team.