The Quaestor - Volume 12, Issue 2
Breadcrumb
- RIT/
- Finance and Administration/
- Institute Audit, Compliance & Advisement/
- The Quaestor - Volume 12, Issue 2
How An Organization’s Three Lines of Defense Effectively Manage Risks
Contributed by: Nancy A. Nasca, Manager, Institute Audit, Compliance & Advisement, naniaca@rit.edu
Each of us, no matter our role, are responsible to carry out day-to-day operations which affect the overall success of RIT. If obstacles to the accomplishment of key organizational objectives are not identified, evaluated, prioritized, and managed, each employee’s ability to effectively perform their designated job responsibilities could be adversely affected. Therefore, it is important that all employees understand their role in risk management and the implementation of internal controls.
The Three Lines of Defense model1, promulgated by the Institute of Internal Auditors, provides a flexible framework that clearly delineates organizational roles and responsibilities for the effective management of risk and control.
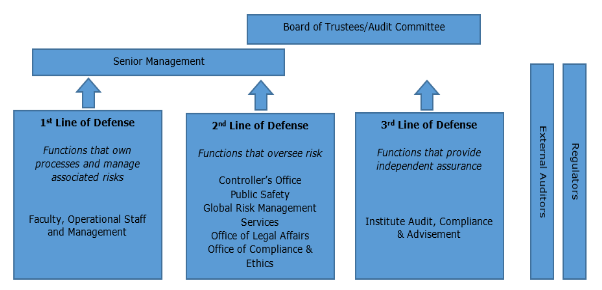
The Board of Trustees and senior management are the primary stakeholders served by the three lines of defense. They have collective responsibility for setting RIT’s objectives, defining the strategies to achieving these objectives, and establishing governance structures and processes to best manage the risks which might prevent the accomplishment of these objectives.
Risk identification is a dynamic process which should be integrated into the day-to-day activities of an organization to facilitate the timely identification of problems that could interfere with the achievement of objectives. Therefore, the first line of defense lies with RIT’s faculty, operational staff and management. As this group of individuals is responsible for the day-to-day activities and processes that contribute to the overall success of RIT, they are in the best position to identify risks to the university as well as to design and implement effective controls to manage these risks.
The second line of defense is comprised of risk management and compliance functions which assist faculty, operational managers, and staff in developing and monitoring processes and controls to mitigate risks. They work closely with the first line of defense to provide subject matter expertise, implement policies and procedures, and identify and monitor known and emerging issues affecting the organization’s risks and controls. These functions have some degree of independence from the first line of defense; however, they are by nature management functions which may intervene directly in modifying and developing the internal control and risk systems.
Internal auditors serve as an organization’s third line of defense. They provide the Audit Committee of the Board of Trustees and senior management with independent and objective assurance on a broad range of objectives, such as the efficiency and effectiveness of operations, safeguarding of assets, reliability and integrity of reporting processes, and compliance with laws, regulations, policies, and procedures. In order to maintain independence and objectivity, Institute Audit, Compliance & Advisement (IACA) may not design or implement controls and may not be responsible for RIT operational day-to-day functions. IACA acts as an advisor in collaboration with the first and second lines of defense to foster effective governance, risk management, and internal controls.
Although external parties are not formally considered to be among an organization’s three lines of defense, external auditors and regulators play an important role in reviewing and reporting on the organization’s control structure, and setting requirements intended to strengthen an organization’s governance and controls. However, the focus of these parties is generally narrower in nature than the scope of responsibilities for the three lines of defense, which are expected to address the entire range of operational reporting and compliance risks facing an organization. Therefore, these external parties should not be considered as substitutes for the internal lines of defense as it is an organization’s responsibility to manage its own risks.
The RIT Board of Trustees and senior management recently began the implementation of an enterprise-wide risk management initiative. As described above, each of the three lines of defense at RIT will play a critical role in the successful execution of RIT’s enterprise-wide risk management processes by identifying, managing, and monitoring risks that may prevent RIT from accomplishing its strategic and operational objectives.
Reference
1 The Three Lines of Defense in Effective Risk Management and Control, The Institute of Internal Auditors, January 2013
Inform RIT
Contributed by: Ben Woelk, Program Manager, RIT Information Security Office, infosec@rit.edu
Inform RIT is a recurring column provided by the RIT Information Security Office. The column highlights current issues and initiatives that impact the RIT community. In this issue, we’ll talk about cybersecurity considerations for traveling abroad. A special thank you to the Assistant Vice President for Compliance & Ethics and Deputy General Counsel in the Office of Legal Affairs for providing information about export controls.
Cybersecurity Considerations for Traveling Abroad
Over the last few months, there has been an increased focus on the risks and policies around travel abroad, including policies around flying with laptops and mobile devices. We were recently contacted by an RIT faculty member traveling to a conference abroad who had questions about securing his laptop. We have provided the information below to help you prepare for travel. A couple of notes:
- This communication reviews Cybersecurity concerns. RIT Global Risk Management Services provides a more comprehensive overview of travel policies and considerations.
- Travel restrictions can change abruptly, both here and abroad. Review the U.S. Department of State Alerts and Warnings before and during travel.
Traveling with a laptop and other mobile devices
Should you bring your RIT laptop?
- It depends. Can you do without it? Unless you need your laptop to conduct university business, we recommend that you do not take it.
Should my laptop be encrypted?
- Probably. Be aware that even on re-entry to the United States, custom agents may examine your laptop.
- Some countries restrict the export of electronic devices (including laptops), software (including encryption software), and other technology. Before travelling internationally, check with the U.S. Department of State to ensure you have up-to-date information on controls that may apply. In some cases, it may be necessary to obtain prior authorization in the form of a license from the country of export or import.
- The export of U.S.-origin technology (from any country), including but not limited to encryption software, may also be prohibited without authorization before it is carried or shipped abroad. Many commercially available electronic devices (e.g., laptops, iPads, cell phones, and digital storage devices) come with pre-loaded encryption software which is subject to export controls administered by the Department of Commerce. Many of these items can be temporarily exported under license exceptions referred to as “Temporary exports-Tools of loaded encryption software which is subject to export controls administered by the Department of Commerce. Many of these items can be temporarily exported under license exceptions referred to as “Temporary exports- Tools of the Trade” (TMP) or Baggage (BAG). Under the TMP exception, when laptops and other devices (including related technology and software) are: used for professional purposes, returned within 12 months, kept under effective control of the exporter while abroad (i.e., kept in a hotel safe or other secured space or facility), and other security precautions are taken against unauthorized release of technology (i.e., use of secure connections, password systems, and personal firewalls), then the TMP license exception might apply. The Baggage (BAG) license exception covers personal items that are owed by the researcher and intended only for their personal use. It is important to note that these license exceptions do not apply generally to embargoed countries, like Cuba, Iran, North Korea, Sudan, or Syria. If you require guidance on export controls prior to travelling, please contact the Office of Compliance and Ethics.
What should I do before my trip?
- Back up all data before your trip.
- If there is confidential information or sensitive information on your computer that will not be needed during your trip and that you don’t want others to see, store it on your network share or other approved back-up device and remove it from the computer that’s traveling with you.
- It may be appropriate for you to talk with your department about taking a loaner laptop on the trip.
What should I do during my trip?
- Assume that your laptop will be examined.
- It is also possible that you may be required to place your laptop in checked baggage. Use a case or container that is designed to protect your laptop if it is checked. (If you do not have a container, place the laptop in the middle of your luggage and use clothing to cushion it.)
- If you are working during the trip, ensure that you are saving to your cloud provider or to USB flash memory.
- Keep your direct access to RIT systems and information resources at a minimum.
- Watch out for distractions and possible theft. If your RIT-owned laptop or device is stolen, please report it to RIT Public Safety, 585-475-2853.
What should I do to prepare for my return home?
- Again, assume that your laptop will be examined and may be placed in checked baggage.
- Consider shipping the laptop back in a suitable container to the United States instead of taking it on your flight.
What should I do when I have returned home?
- When you return home, change your passwords.
- Contact your service desk to erase and re-image your hard drive and other components.
- Restore your data.
For more information
- RIT Travel Guidelines https://www.rit.edu/fa/grms/academic_fieldtrips.html
- RIT International Traveler Emergency Response Plan https://www.rit.edu/fa/grms/academic_fieldtrips.html
- U.S. Department of State Travel Alerts and Warnings https://travel.state.gov/content/passports/en/alertswarnings.html
- Bureau of Industry and Security, U.S. Department of Commerce – Export Administration Regulations https://www.bis.doc.gov/index.php/regulations/export-administration-reg…
- Bureau of Industry and Security, U.S. Department of Commerce – Encryption FAQs https://www.bis.doc.gov/index.php/policy-guidance/encryption/encryption…
- Government Bans Electronics on US Bound Flights from 10 Airports https://arstechnica.com/tech-policy/2017/03/government-bans-electronics…
Sign up for our DSD101 course, Introduction to Digital Self Defense through CPD.
Guest Author Article: Controller’s Office
Accounting for Fixed Assets at RIT
Contributed by: Milagros Concepcion, Assistant Controller, Controller’s Office, mxlcto@rit.edu
Property Accounting, a unit within the Controller’s Office Accounting Operations department, is responsible for ensuring RIT’s fixed assets are accounted for in accordance with accounting standards and working with departments campus-wide to ensure they are tracked and safeguarded. They share these responsibilities with faculty and staff campus-wide.
Property Accounting staff are responsible for:
- Establishing processes and procedures to ensure departments adhere to the university’s and federal government’s property standards;
- Maintaining RIT’s asset recordkeeping system which includes capital equipment, land, buildings, and building and site improvements;
- Managing the annual physical inventory process;and
- Updating the recordkeeping system regularly with all changes including acquisitions and retirements.
Departmental faculty and staff are responsible for:
- Following RIT’s procurement standards for capital equipment;
- Ensuring that assets are safeguarded;
- Completing annual physical inventories; and
- Reporting asset retirements and disposals to Property Accounting timely.
The university evaluated the current capital equipment threshold of $1,500 and a decision was made to increase the threshold to $5,000 or more, effective July 1, 2017 (FY18). The current threshold has been in place since July 1, 1996 (FY97). All other criteria used to define capital equipment will remain unchanged.
The current university policy defines capital equipment (including furniture and furnishings) as an article of nonexpendable, tangible (moveable) personal property with a useful life of more than one year and an acquisition cost (including delivery and installation charges) of at least $1,500 ($5,000 effective July 1, 2017). Capital equipment with a cost of at least the capitalization threshold must be capitalized and depreciated over the useful life of the asset. Any equipment costing less than the capitalization threshold is expensed in the same month it is purchased.
You might be wondering, why not sooner?
The university recovers a portion of its depreciation expense through the Facilities and Administration (F&A) rate applied to federal grants and contracts. The university’s current organized research rate is 46.5%, and because this percentage was calculated using depreciation for assets under the $1,500 threshold, federal regulations required that the change be made once the current F&A rate agreement expires; that date is 06/30/2017.
The benefits
Once this change takes effect, fixed assets volume will decrease by approximately 60% while 83% of the capital equipment value will be preserved. This change will significantly reduce the administrative burden on the Property Accounting staff and the faculty and staff university-wide who currently track capital equipment assets until they are disposed or retired. This will also enhance overall stewardship and control of the university’s assets by eliminating the requirement to track relatively low value items, and in turn, devoting more attention and effort to safeguarding higher valued items.
How does this change affect me?
| Received (regardless of when it was or- dered) or Fabrication completed |
New equipment - unit acquisition cost or Fab- ricated equipment - overall cost |
Accounting Treatment | Object Code / Project |
|---|---|---|---|
| On or after 7/1/2017 | $5,000 or more | Capitalized | 16200 – Capital Equipment; typically your 84200 project |
| Less than $5,000 | Expensed | 84000 – Supplies |
Begin using $5,000 as the capital equipment threshold on new purchase requisitions for items to be received on July 1st or later. If the equipment will be received before July 1, 2017, follow the $1,500 capitalization threshold.
The Controller’s Office staff have begun sending communications university-wide and will publish revised policies, process and procedures and all applicable forms on the Property Accounting website prior to the effective date of July 1, 2017.
If you want to learn more about Property Accounting – consider registering for the Accounting Practices, Procedures and Protocol: Accounting for Fixed Assets and Capital Projects workshop offered through the Center for Professional Development.
Committee of Sponsoring Organizations of the Treadway Commission (COSO) Corner
Contributed by: Nancy A. Nasca, Manager, Institute Audit, Compliance & Advisement, naniaca@rit.edu
As explained in previous editions of the Quaestor Quarterly, the COSO Framework (an internationally recognized standard with which the adequacy and effectiveness of an organization’s internal controls are evaluated) was updated in May 2013 to further define the principles underlying the five components of internal control (Control Environment, Risk Assessment, Control Activities, Information and Communication, and Monitoring). According to the Framework, these principles are fundamental concepts that must be present and functioning in order to achieve an effective system of internal control.
In addition, the Framework includes points of focus or characteristics that are examples of behaviors or processes that would be expected to be in place to demonstrate that the related principle is in fact present and functioning. This edition of the COSO Corner will summarize the eleventh COSO principle, which is the second principle related to the Control Activities component of the COSO Framework, as well as the related points of focus.
Principle 11 – The university selects and develops general control activities over technology to support the achievement of objectives. When designing and implementing technology-related control activities, management should consider:
- The Dependency Between the Reliability of Business Process Technology and Technology General Controls – Technology general controls over the acquisition and development of technology are implemented to help ensure that automated controls work properly to support the security, integrity, effectiveness, and efficiency of information systems.
- The Establishment of Technology Infrastructure Control Activities – The technology infrastructure includes, but is not limited to, servers, networks, operating systems, application software, and data interfaces. The technology infrastructure at RIT is a combination of centralized and decentralized functions adding an additional level of complexity which presents risks that need to be understood and addressed. Control activities over the technology infrastructure are designed and implemented to support the completeness, accuracy, and availability of technology processing.
- The Establishment of Security Management Process Control Activities – Security control activities are designed and implemented to restrict technology access rights to authorized users commensurate with their job responsibilities and to protect the university’s assets from external threats (i.e., phishing attacks). RIT’s Information Security Office has established minimum standards to provide leadership to the RIT community in safeguarding the confidentiality, integrity, and availability of RIT’s information resources. You can view these standards at: http://www.rit.edu/security/content/intro-policies-standards.
- The Establishment of Technology Acquisition, Development, and Maintenance Process Control Activities – A technology development methodology (i.e., Systems Development Life Cycle) provides a structure for system esign and implementation, and outlines documentation requirements, approvals, and checkpoints with controls over the acquisition, development and maintenance of technology. This methodology also provides appropriate controls ver changes to technology, which may involve requiring authorization of change requests and standard protocols to determine whether changes are made properly.
Similar to business transaction controls, technology general controls may include both manual and automated control activities. The extent and rigor of technology general controls will vary depending on various factors such as the complexity of the technology and risks associated with the underlying business process being supported.
Reference
Committee of Sponsoring Organizations of the Treadway Commission (May 2013). “Internal Control – Integrated Framework – Framework and Appendices”
Additional Information by IACA
Watch IACA’s Monday Minute video series here!
Our video series focuses on opportunities for improving internal controls and increasing awareness of various university processes, policies, and protocols. If you have questions, feel free to contact anyone in the IACA office using information on our webpage.
Just to name a few, past topics include: Travel Policy changes, FERPA Regulations, RIT’s Ethics & Compliance Hotline, Records Management Policy, Risk Assessment, and many others.
What about ethics in the workplace?
Learn about the RIT Ethics and Compliance Hotline
IACA Team
Learn more about your IACA team.