Private Information Management Initiative
Overview
Private Information Management Initiative (PIMI) Overview
The Private Information Management Initiative seeks to identify and reduce the amount of Private Information found on RIT computers and storage devices. Private information is information that is typically used to conduct identity theft and may include Social Security Numbers (SSNs), credit card numbers, driver’s license numbers, bank account information, etc.
Reducing the amount of Private Information (PI) will help safeguard the RIT community against identity theft and will help RIT comply with relevant state and federal laws.
Goals
- Increase awareness of the importance of safeguarding all private information, not just SSNs
- Increase awareness of the existing RIT policies that address private information
- Increase sense of individual accountability and responsibility in the area of policy compliance surrounding private information and a related understanding of the consequences for noncompliance
- Effective destruction of non-approved and unnecessarily retained private information (paper and electronic forms) from business units and employee offices
- Integration of the Records Management Policy into everyday employee activities
Representation
RIT Information Security Office (ISO) is leading this initiative with the assistance of project team representatives from each college and division. The representatives include:
- An Information Steward/Management Representative who will receive reports detailing the location of Private information and will lead remediation efforts of Private information found in electronic and paper forms.
- A Technical Representative who will assist in inventorying computers assigned to the respective college or division and will assist the Information Steward/Management Representative in remediation efforts.
- Current list of representatives
What to Expect
ISO is working with various RIT organizations to identify the location of SSNs and other Private Information by providing a software tool (Microsoft Purview) that will scan computers and attached drives to determine if they contain Private information. When Microsoft Purview finds suspected Private information, it provides a report to the computer user and to the ISO. The software also provides the computer user with tools to erase (shred) the information securely or to remove (redact) the private information from the files.
Scans will be initiated by ITS. Computer users may also initiate an on-demand scan at their convenience. Microsoft Purview is licensed for use on RIT-owned computers and is currently available for Windows and Macs.
For More Information
For more information, contact the ISO.
IAP Plan Requirements
IAP Plan Requirements and Template
Excerpted from the Information Access and Protection Standard
- Information Inventory
- All RIT organizational units (departments, divisions, etc.) should identify and maintain an inventory (type, classification, location, accessibility) of all Private, Confidential, and Internal information they handle or maintain. The ISO provides an Information Access and Protection Plan Template to facilitate this requirement. (The plan should be updated at least annually.)
- Training
- Divisional VPs and Deans are responsible for ensuring that mandatory information handling training is provided to any RIT employees (including adjuncts, temporaries and contractors), student employees, volunteers (including trustees, agents, members of affiliate groups, etc.) with access to Confidential or Private information.
- This training should be conducted on an appropriate periodic basis. (Annually is appropriate, and can be fulfilled through the self-paced web-based RIT Information Handling, available through the Talent Roadmap.)
- Non-disclosures
- Divisional VPs and Deans are responsible for ensuring that users comply with RIT non-disclosure requirements, which may include signing a non-disclosure agreement.
- Systems, applications, or web page administrators (including student employees) who administer information systems containing Confidential or Private information should sign the RIT Systems Support Personnel Non-Disclosure Agreement form.
Resources
- Information Access and Protection Plan Template (The template provides instructions, examples of information classifications, and an inventory with examples.)
Frequently Asked Questions
The Private Information Management Initiative (PIMI) is a program where RIT Information Technology Services helps RIT faculty and staff scan their computers and attached drives to determine if they contain private information (PI). When PI is found, each RIT faculty and staff member is responsible for remediating the private information by redacting or shredding the files.
The program also includes destruction of paper files containing nonessential PI.
The goals of the program are to identify and reduce the amount of private information at RIT. This reduction will help safeguard the RIT community against identity theft and will help RIT comply with relevant state and federal laws.
New York State defines private information (PI) as:
any personal information concerning a natural person combined with one or more of the following data elements: Social Security number (SSN), driver's license number, account number, or credit or debit card number in combination with any required security code. These combinations of information are often used in identity theft.
The New York State Information Security Breach and Notification Act requires that RIT notify affected consumers if their Private information is compromised.
RIT is scanning your computer or drive because we've found that scans have revealed the presence of Private information on many computers; even when the computer owners do not believe there is any Private information present. We want to reduce the potential for identity theft occurring as a result of information obtained from RIT computers.
RIT is authorized to scan computers using the RIT network in order to protect the RIT community. See the Computer Code of Conduct and Network Use and the Privacy Policy.
It is important to note that ITS may inspect the results of the scan only to aid in remediation efforts.
Many universities scan for Private information on computers connected to their networks and have begun remediation of paper files and other media containing Private information.
Your computer is scanned by Microsoft Purview software installed on your computer. The scans will be initiated from a central scanning server administered by ITS. Microsoft Purview also allows you to initiate an on-demand scan. You do not have to be connected to the network to initiate an on-demand scan.
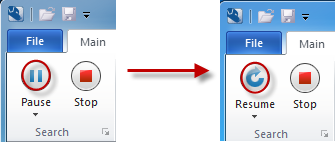
It's easy to pause Microsoft Purview so that it doesn't impact your productivity significantly. Go to your system tray, right click on the Microsoft Purview icon (Ctrl-click for Mac) and choose Maximize. Then click on the Pause button. When you're ready to resume the scan, click on Resume.
Microsoft Purview will generate an interactive report of suspected Private information matches and provide user-friendly tools to erase the information securely or remove the Private information (e.g., Social Security Number, Bank Account Number, Credit Card Number or Drivers License) from the files directly from the interactive report. You may also identify "false positives" by choosing "Ignore" within IDF. ITS may verify that the ignored files do not contain Private information.
When Microsoft Purview completes its search, review the list of results to begin Shredding or Redacting Private Information and Ignoring "false positives."
You can choose shred, redact, or ignore by right-clicking on the check box next to the entry and choosing from the options available. NOTE: not all options are available for all file types. Process the entire list before closing Microsoft Purview.
If Microsoft Purview completes its search and no Private Information is found, close Microsoft Purview.
If you are unable to "shred" a file containing Private Information, you may not have permissions in Windows that allows Microsoft Purview to "shred" it. Contact the RIT Service Center and ask them to login to Microsoft Purview as admin and securely "shred" the file.
Microsoft Purview provides a redact option for specific file types that may not work with all file types. If you need to retain an Office file on your computer but need to redact the Private information in the file you’ll need to follow a three-step process.
- Save a copy of the file in Office 2007 or 2010 format (.docx, xlsx, etc.).
- Use Microsoft Purview to redact the Private information from the new file.
- Use Microsoft Purview to shred the old file.
We've created a Private Information Handling Quick Reference Table to assist you in determining how to handle Private information found on your computer or drives.
If you find Private information (e.g. Social Security Number, Bank Account Number, Credit Card Number or Drivers License) on your computer and are not sure whether it should be there, ask your Information Steward/Management Representative.
New York State law does not allow the retention of Social Security Numbers unless there is a clear business need for the information. In general, an RIT employee has a legitimate purpose for having access to the Social Security Numbers of another individual when such number is required for tax or billing purposes, credit authorizations, background checks, or in furtherance of submitting a federal or state governmental application that requires the transmission of an individual's Social Security Number. In addition, social security numbers shall be maintained when required by either court order, subpoena, or by direction of the Office of Legal Affairs.
Unless required by RIT business processes, files must not contain Private information. Unnecessary information must be sanitized by redacting (removing) the Private information. It is not sufficient to simply obscure or hide the information. Although "redaction" has a broader meaning in editing, in the context of information handling it refers to the removal of information from a document.
Private information should not be stored on an RIT computer unless expressly permitted. (This information is typically found in copies of tax returns and filled-in forms.)
Currently, only computers with the Microsoft Windows and Mac OSX will be scanned by Microsoft Purview. We encourage you to examine the files on your computer and attached drives to identify Private information and handle it accordingly. For Linux, we recommend using Cornell's Spider. You may also work with your systems administrator to scan the Linux drive from Windows.
Please direct any questions regarding information handling or the Private Information Management Initiative to your Information Steward/Management Representative.
PIMI Representatives
|
Organization |
VP / Dean |
Information Steward / Management Representative |
Technical Representative |
|---|---|---|---|
|
Administration |
|||
| Office of the President | William Sanders | Karen Barrows | RIT Service Center (John Mander) |
| Enrollment Management | Kathleen Davis | Colleen Peterson | RIT Service Center |
| Finance & Administration (F&A) | Jim Watters | Joan Graham | ITS (John Mander, Mason Lezette, Shaair Codner, Alan Blumenstock) |
| Global Risk Management Services | Jim Watters | Melinda Ward | RIT Service Center |
| Information and Technology Services (ITS) | Jim Watters | Joan Graham | |
| Marketing & Communications | John Trierweiler | Steven Wunrow | David Scheiderich |
| RIT Inn & Conference Center | Milagros Concepcion | Bill Gunther/Janice Kuhn-Emerson | RIT Service Center |
| Student Affairs | Sandra S. Johnson | Jodi Boita/Jessica Bowen | RIT Service Center |
| University Advancement | Phil Castleberry | Patrick Saeva | Emily Ferguson/RIT Service Center |
| University Communications | John Trierweiler | Bob Finnerty | RIT Service Center |
|
Academic Administration |
|||
| Provost / Academic Affairs | Prabu David | Emily Redman/Josh Pemberton | RIT Service Center |
| Center for Teaching and Learning (CTL) | Neeraj Buch | Neil Hair | RIT Service Center |
| Diversity and Inclusion | Keith Jenkins | Sandy Whitmore | RIT Service Center |
| Government and Community Relations (GCR) | Vanessa Herman | Michelle Lezette/Lori Gentile | RIT Service Center |
| Office of Co-op Education & Career Services | Neeraj Buch | Maria Richart | Jim Bondi/RIT Service Center |
| Office of International Education and Global Programs | Prabu David | James Myers/Lyndsey McGrath | RIT Service Center |
| Office of the Registrar | Neeraj Buch | Joe Loffredo | RIT Service Center |
| RIT Libraries / RIT Press | Prabu David | Eric Blevins | Ryan Ammerman/Justin Newcomer |
| Sponsored Research Services | Ryne Raffaele | Denis Charlesworth | RIT Service Center |
| University Advising Office | Neeraj Buch | Lynne Mazadoorian/Dewey Lawrence | RIT Service Center |
|
Colleges |
|||
| College of Art and Design (CAD) | Todd Jokl | Michael Dear | Rob Henderson/Joe Schultz |
| College of Engineering Technology (CET) | S. Manian Ramkumar | Steven Praino | Michael Good |
| College of Health Sciences and Technology (CHST) | Tai Wang | ITS (Charles Hall) | |
| Center for Integrated Manufacturing Studies (CIMS)/ Golisano Institute for Sustainability (GIS) | Nabil Nasr | Scott Nichols | Brian Camp |
| Center for Imaging Science (CIS) | Andre Hudson | Jan Van Aardt | Brett Matzke / Karen Braun |
| College of Liberal Arts (CLA) | Kelly Martin | Lauren Hall | ITS (Omar Chin) |
| College of Science (COS) | Andre Hudson | Larry Buckley | ITS (Zack Green) |
| B. Thomas Golisano College of Computing and Information Sciences (GCCIS) | Matthew Huenerfauth | Charles Gruener | James Brigden |
| Kate Gleason College of Engineering (KGCOE) | Doreen Edwards | ITS (Logan Thompson) | |
| National Technical Institute for the Deaf (NTID) | Gerard Buckley | Stephanie Tolan | Michael Stanko |
| NTID - Substance & Alcohol Intervention Services for the Deaf | Gerard Buckley | Bernard Hurwitz/Mary Karol Matchett | Keven Poore |
| RIT Graduate School | Diane Slusarski | Bella Dunwoody | RIT Service Center |
| Saunders College of Business (SCB) | Jacqueline Mozrall | Dave Ballard | Dave Ballard |
| University Studies | James Hall | Abby Cantwell | ITS (Ryan Brown) |
Updated: 05/2025
Faculty and Staff Responsibilities
All RIT faculty and staff are expected to follow the Private Information Management Initiative (PIMI) requirements below:
- Review paper files for private information.
- Scan RIT computers with Microsoft Purview for private information (if Microsoft Purview is not available, scanning with an alternative tool or reviewing the computer for Private Information is recommended). Information Technology Services (ITS) will initiate scans of most computers monthly.
- Scan or review personal/home computers, portable devices, and media for private information.
- Inform your manager in writing if there is a compelling business reason for retaining private information. Promptly secure the information in compliance with the RIT Information Access and Protection Standard.
- Notify and receive approval from your PIMI Information Steward/Management Representative.
- If you're unable to remediate the information found within Microsoft Purview, please redact (securely erase or securely destroy) unnecessary private information.
- Complete the Digital Self Defense 103 Information Handling course.
Additional Requirements for Department Managers
- Ensure faculty and staff have reviewed paper files and scanned or reviewed electronic files.
- Ensure faculty and staff have redacted, securely erased or securely destroyed unnecessary private information.
- Receive authorization to retain any private information from the Divisional VP/Information Steward/Management Representative.
- Secure the remaining private Information in compliance with the RIT Information Access and Protection Standard.
Private Information Handling Quick Reference Table
This table provides recommendations on the correct handling of private information at RIT.
New York State defines private information (PI) as any personal information concerning a natural person combined with one or more of the following data elements: Social Security number, driver's license number, account number, or credit or debit card number in combination with any required security code.
Digital Self Defense 103 - Information Handling fulfills the training requirement for handling RIT Private or Confidential Information.
Consult the Microsoft Purview End User Documentation for Windows or Mac for more information.
|
Situation |
Microsoft Purview Instructions (Preferred) |
General Instructions (Use if Microsoft Purview is NOT available) |
|---|---|---|
|
I no longer need the files containing the private information |
Delete the files using the "Shred" command. This can be done from within the Microsoft Purview interactive scan report or by right-clicking on the file or folder and choosing "Identity Finder/Shred." If you are unable to delete the file, contact your help desk. |
Delete the files securely. Use a secure file deletion utility such as Eraser. Contact your systems administrator or the RIT Service Center for recommended products. |
|
I need to keep the files, but I don't need the private information |
Sanitize the information by using the "Redact" command. This can be done from within the Microsoft Purview interactive scan report. Microsoft Purview will replace the Private Information with x's. Note that this option is not available for all file types. |
Sanitize the documents by deleting any private information such as Social Security Numbers (SSNs) or credit card numbers. Save a new copy of the sanitized document and delete the original file. |
|
I need to continue to have a unique identifier for each individual |
Sanitize the information by using the "Redact" command. This can be done from within the Microsoft Purview interactive scan report. Microsoft Purview will replace the Private Information with x's. Open the file and replace the x's with unique identifiers not based on the SSN. |
Sanitize the documents by eliminating the private information. Convert SSNs to University Identification Numbers (UIDs). |
|
Situation |
General Instructions for Handling Private Information |
|---|---|
|
I need to keep the complete files containing the private information |
Unnecessary possession of Private information should be eliminated.
In addition, SSNs shall be maintained when required by either court order, subpoena, or by direction of the Office of Legal Affairs.
Contact the RIT Service Center or the RIT Information Security Office for more recommended practices. |
|
I need to carry the files on a portable computer, device, or media (e.g., Laptops, Flash Drives, CD/DVDs, smartphones) |
Unnecessary possession of Private information should be eliminated.
In addition, SSNs shall be maintained when required by either court order, subpoena, or by direction of the Office of Legal Affairs.
Inform your manager and your Information Steward/Management Representative of the need to retain Private information. |
|
I no longer need the portable media or hard drive, how do I dispose of them securely? |
The RIT Information Security Office provides the following secure disposal recommendations:
A degausser and media shredder are available at the RIT Service Center in Booth 07B. |
Media Disposal Recommendations
| Media | Disposal Method |
|---|---|
|
Paper |
Use a shredder. Crosscut is preferred over a strip shredder. Disposal of paper records containing Private or Confidential information should be accomplished by crosscut (or better) shredding, placement in a locked document destruction bin, or through vendor-supplied services under a contract approved by RIT Procurement Services. |
|
CD, DVD, diskette, etc. |
Use the media shredder (contact the RIT Service Center). |
|
Hard Drives |
If the hard drive is to be reused, contact your support organization for recommendations for secure erasure. If the hard drive is damaged or will not be reused, render the hard drive unreadable by using the degausser (contact the RIT Service Center). Note, that Solid State Drives (SSds) may not be sufficiently disrupted by the degausser. |
|
Tapes |
Use the degausser (contact the RIT Service Center). |
|
Solid State Drives (SSDs) |
Overwrite and destroy media though methods including shredding, disintegrating, or pulverizing. |
|
Other |
Use an industry standard means of secure disposal. |
Links to guidelines for media sanitization:
Document Destruction
Document Destruction
Document Destruction Activities provide a focused opportunity for RIT faculty and staff to archive securely or dispose of paper records that contain private information. Private Information includes financial account numbers, social security numbers, driver’s license numbers and other information that can be used in identity theft. Participation in this activity will enable RIT to secure Private Information that could otherwise be used to facilitate identity theft. Document Destruction Activities are part of the RIT Private Information Management Initiative, but they are managed by your department. We encourage all departments to schedule Document Destruction Activities.
Why are Document Destruction Activities so important?
With its concentration of student records and private information, Higher Education is often targeted by attackers hoping to harvest private information (e.g. Social Security Number, Bank Account Number, Credit Card Number or Drivers License) for use in identity theft. In addition, careless storage or loss of records often leads to data breaches that require compliance with various state and federal laws requiring notification of affected consumers.
Participation in Document Destruction Activities will reduce the likelihood for the RIT community to have their personal information fall victim to malicious attacks or loss. This activity will also provide an opportunity for faculty and staff to adhere to the RIT Records Management Policy (C22.0). Any questions regarding the appropriate retention period can be addressed to the RIT Office of Legal Affairs.
When are my Document Destruction Activities?
Contact your Private Information Management Initiative representative to find out what activities are being planned in your college or division for document destruction.
What do I need to do for my Document Destruction Activities?
It is important that you keep track of any documents that may leave another person susceptible to identity theft attacks. In preparation for your department’s Document Destruction Activities, please review the files in your office to ensure that you have not retained any private information (e.g. Social Security Number, Bank Account Number, Credit Card Number or Drivers License) that is not critical to your current work. Take this opportunity to review files and dispose of them in accordance with the RIT Records Management Policy (C22.0).
We encourage you to review your files now and dispose of those containing Private Information securely. Ensure that any RIT files in your home do not contain any private information.
How do I dispose of portable media and paper documents containing Private Information securely?
Visit our Information Disposal page for recommendations.
What if I have questions?
Contact your division or college's PIMI representative.
