8,959,348
Methods Establishing a Symmetric Encryption Key and Devices Thereof
Synopsis
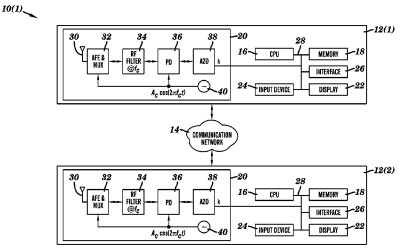
Patent US 8,959,348 B2 describes methods and devices for establishing a symmetric encryption key. This invention presents a novel approach to generating secure symmetric encryption keys between two or more communication devices without the need for a prior shared secret or complex public-key infrastructure. This significantly simplifies and enhances the security of wireless and wired communications.
A key novel aspect of this invention lies in its reliance on shared environmental characteristics to derive a common secret key. Instead of exchanging cryptographic material, the communication devices measure and leverage a common, naturally occurring phenomenon, such as channel noise, phase differences in a carrier signal, or signal strength fluctuations, that is unique and unpredictable to external eavesdroppers but observable by the legitimate communicating parties. The patent details a process where both devices independently measure this shared environmental characteristic, quantize it, and then use a consensus algorithm to agree on a secret key. This method intrinsically links the key generation to the physical environment, making it highly resistant to conventional eavesdropping attacks and eliminating the complexities of key distribution.
The commercial potential for this symmetric encryption key establishment system is substantial across various sectors requiring secure and convenient communication:
-
Internet of Things (IoT) Devices: The proliferation of IoT devices demands robust yet simple security solutions. This technology allows resource-constrained IoT devices to establish secure connections without complex pre-configuration or computationally intensive public-key cryptography, enabling secure communication for smart homes, industrial sensors, and wearable technology.
-
Wireless Communication Networks: From Wi-Fi to cellular networks, this invention can enhance the security of connections by providing an on-demand, dynamic key generation mechanism that is resilient to attacks. This is particularly beneficial for transient connections or ad-hoc networks where traditional key management is challenging.
-
Industrial Control Systems (ICS) and SCADA: In critical infrastructure and industrial automation, secure communication between sensors, actuators, and control units is vital. This technology offers a robust way to establish secure channels, protecting against cyber-physical attacks and ensuring operational integrity.
-
Automotive and Vehicular Communication (V2V/V2I): As vehicles become increasingly connected, secure communication between vehicles (V2V) and between vehicles and infrastructure (V2I) is crucial for safety and autonomous driving. This method can enable secure, dynamic key agreement for vehicle-to-vehicle communication, securing sensitive data exchange.
-
Tactical and Military Communications: In dynamic and hostile environments, rapid and secure communication establishment is paramount. This invention offers a resilient and difficult-to-intercept method for generating shared secrets, even in scenarios where traditional key exchange methods might be compromised or impractical.
-
Personal Area Networks (PANs) and Wearables: For devices like Bluetooth headphones, smartwatches, or health monitors, establishing secure connections can be simplified. The environmental key generation can provide a seamless and secure pairing experience without manual input or complex setup.
This invention provides a paradigm shift in symmetric key establishment by exploiting shared physical phenomena, offering a secure, efficient, and user-friendly solution for a wide array of communication applications. Its ability to simplify secure connectivity, especially in environments with limited resources or dynamic network topologies, positions it as a foundational technology for next-generation secure communication systems.