Quaestor Volume 18, Issue 1
- Audit Considerations for Compliance and Legal Risks
- RIT Partners with PaymentWorks to Provide a Secure Portal for Supplier Onboarding
- A Mindful Approach to Information Security and System Integrity
- Do you know anyone who is not receiving the Quaestor?
- Training Opportunities Provided by IACA
- Additional Information by IACA
Audit Considerations for Compliance and Legal Risks
Contributed by: Nancy Nasca, Associate Director, Institute Audit, Compliance and Advisement
It's important for everyone on campus to be familiar with laws and regulations affecting their areas of responsibility. Do you know the laws and regulations affecting your area of responsibility?
One of the risks that Institute Audit, Compliance and Advisement (IACA) considers when developing our audit plan and each engagement scope is the significance of compliance and legal requirements for the operations of the department or process under review. The RIT Community is subject to many compliance and legal requirements not only from Federal, State, and Local governments, but also from accrediting and sanctioning organizations (i.e., Middle States Commission on Higher Education, National Collegiate Athletic Association), sponsoring organizations, and university policies and procedures.
Depending on your role at RIT, it is important that you understand the key compliance and legal requirements that directly affect your area of operations. RIT’s Code of Ethical Conduct and Compliance requires that members of the university community be familiar with the laws and regulations affecting their areas of responsibility. Other RIT policies and procedures provide minimum standards to promote compliance with relevant laws and regulations including, but not limited to:
- D15 – Education Records – addresses RIT’s implementation of the Family Educational Rights and Privacy Act of 1974 (FERPA).
- C26 – Protection of Minors Policy – the procedures in this policy provide reporting requirements for activities involving Minors as well as program registration, staffing, and supervision requirements.
- C27 – Policy on Title IX Sexual harassment for Faculty, Staff, and Students – defines key terms, care, support, and reporting options, and the Title IX grievance process required by the final rule issued by the U.S. Department of Education on May 19, 2020 under Title IX of the Education Amendments of 1972.
- Foreign Corrupt Practice Act (FCPA) Policy – includes information about the implementation and compliance with the FCPA which prohibits bribery of foreign officials and employees who work for foreign governments.
- Administrative Policy and Procedures for Externally Sponsored Projects – provides administrative guidance to ensure compliance with legal, regulatory, contractual, and ethic requirements established by sponsoring organizations.
Another important aspect of promoting compliance with laws, regulations, and accrediting and sanctioning body organizational standards is providing training to faculty, staff, and students. RIT’s Office of Talent Development offers training on a large variety of compliance and legal topics including but not limited to Employment Law, Occupational Safety and Health Administration (OSHA), Payment Card Industry (PCI), FERPA, Export Controls, American with Disabilities Act (ADA), Discrimination and Harassment (including Title IX), The General Data Protection Regulation (GDPR). In addition, there are numerous external resources available (i.e., professional association, accrediting and sanctioning organization, and governmental websites and conferences) to educate RIT faculty, staff and students on compliance and legal requirements. The Higher Education Compliance Alliance is a great resource to obtain information regarding laws and regulations relevant to universities.
Ultimately, it is each employee’s responsibility to ensure that they are aware of the key regulations which affect their area of operations and to discuss any questions or concerns regarding compliance with these laws with your supervisor or other knowledgeable resources available to the RIT community (i.e., Office of Legal Affairs, Office of Compliance and Ethics, Global Risk Management Services, Information Security Office, Human Resource Department).
RIT Partners with PaymentWorks to Provide a Secure Portal for Supplier Onboarding
Contributed by: Milagros Concepcion, Associate Vice President/Controller and Assistant Treasurer
We are excited to announce that RIT has partnered with PaymentWorks to provide an easy-to-use and secure web portal that businesses and individuals will use to complete the supplier onboarding process. Demonstration sessions will be available on April 5th and 12th. See within for additional details!
We are excited to announce that RIT has partnered with PaymentWorks to provide an easy-to-use and secure web portal that businesses and individuals will use to complete the supplier onboarding process. Departmental users will log-into the PaymentWorks system using their RIT credentials with the following link https://www.paymentworks.com/login/saml/?idp=rit and send invitations to prospective suppliers. The supplier will use the PaymentWorks portal, free of cost, to provide banking and other identity information to create their account. Once PaymentWorks verifies the information, the departmental user and supplier will receive a notification that the set up process is complete.

There are minimal requirements to initiate this process, and once completed, this free service will allow suppliers to:
- View the status of invoices
- Access remittance details
- Maintain supplier master information
- Avoid delays in payment due to incorrect check remit address or other critical data
- Turn on ACH Payments by providing banking information in a secure environment
Why are we making this change?
RIT has partnered with PaymentWorks, as many other organizations and higher education institutions have done, to assist the university in validating information provided by suppliers and automate certain steps such as checking various state and federal sanction and debarred lists. This solution also allows suppliers to provide sensitive information in a secure format and eliminates the need for departments to complete paper forms and manually gather, circulate and store supplier information.
What is changing and when is this change happening?
Effective Monday, April 3rd, all new suppliers will be onboarded using PaymentWorks. Departmental users can log into PaymentWorks using their RIT credentials with the following link https://www.paymentworks.com/login/saml/?idp=rit. Today, departmental users complete paper forms, gather information from the prospective suppliers and attach those documents to a ticket in the RIT Service Center (RSC) with a request to create a supplier record. That process will be discontinued as of the effective date for the change to PaymentWorks, Monday, April 3rd.
In the next week or so, the Controller’s Office will distribute additional information about this new process. In the meantime – SAVE THE DATE for the following demonstration sessions:
Wednesday, April 5 at 9 a.m. https://rit.zoom.us/s/93670986554
or Wednesday, April 12 at 2 p.m. https://rit.zoom.us/s/98957710754
Both sessions will be held in Zoom and have identical content, the first half hour will be a demonstration followed by a half hour dedicated to your questions. We look forward to seeing you there!
A Mindful Approach to Information Security and System Integrity
Contributed by: Rachel Rohrbaugh, RIT Student Employee reporting to Ben Woelk, Governance, Awareness, & Training Manager, Information Security Office (ISO)
By drawing parallels with real-life examples we explain the foundations of a mindful security outlook and its importance to information security. Also, see details within for the ISO's first Cybersecurity Fair on March 31st!
The Security Mindset
The typical perception of cybersecurity is that it stays firmly within the scope of technical controls. Its core, however, what lies beneath every technical action, is an assessment of human behavior and thought. A security mindset evaluates an asset based on its structural merit and considers how an adversary might exploit or take advantage of its processes. The nontraditional approach that a security mindset represents does not need to be an innate trait or inclination. Anyone can learn to use antagonistic reasoning to find areas where value can be imparted. This mindset will lead to deeper topic understanding and improved security practices.
Growth and Development
Cyber security professionals are quick to recognize this value in large part due to their close relations with criminals and their attack styles. Successful attacks by threat actors necessitate ingenuity. To protect against these harmful intents, technical personnel adopt a way of looking at systems from the perspective of opposition. No matter what area of work you are in, developing a security mindset will help you make informed decisions. So, how is a security mindset encouraged and fostered?
When you approach a situation, practice trying to understand your circumstances through a security mindset. For example, consider the habits of bumblebees. The traditional relationship between bees and flowers is the collection of nectar in exchange for pollination. Sometimes though, a bee will do something called “nectar robbing” where they go outside of the flower to where the nectar is expected to be and bite a hole directly into the source. The nectar is easily extracted and the flower never gets pollinated. This then becomes a weakness in the flowers’ structure that is repeatedly used by other bees as an easy entrance without any disincentives to stop their behavior. The flower suffers as a result of this, unable to address an issue its physiology didn’t anticipate.
Practice and Implementation
By breaking traditional thought patterns and considering these kinds of scenarios, you will begin to see where weak points exist and how they can be used to compromise a system’s integrity. This new knowledge can be translated into driving security-conscious improvements.
Gamification is another great way of breaking typical thought patterns by capitalizing on human nature as a tool for learning. Games aid in normalizing and inspiring alternative approaches to problem-solving. Simulations designed for this are wonderful tools for practicing and learning the benefits of a security mindset.
Come Play With Us!
To put this valuable mental approach into action, the RIT Information Security Office is hosting our first Cybersecurity Fair this year in late March. We’ll help you develop a security mindset through activities that promote nontraditional thinking in the form of cryptography puzzles, creating your own scams and phishing attempts, and teaming up to experience our cybersecurity escape room.
If you would like to see how our office is teaching immersive ways of understanding security, join us on March 31st! The Cybersecurity Fair will take place on March 31st in the Fireside Lounge (located on campus in the SAU) between 9:00 AM and 12:00 PM . Additionally, our Keynote Speaker will be presenting in Golisano Hall, Room GOL 1400, from 3:00 PM - 4:00 PM. We hope to see you there!
Do you know anyone who is not receiving the Quaestor?
Through the Staff Council and individual inquiries, it has come to our attention that members of the RIT Community have not been receiving IACA’s newsletter “The Quaestor.” The process of creating and disseminating The Quaestor changed when RIT transitioned to RITmail and we believe that certain elections made when the initial roll-out occurred may have led to this situation.
Through the Staff Council and individual inquiries, it has come to our attention that members of the RIT Community have not been receiving IACA’s newsletter “The Quaestor.” The process of creating and disseminating The Quaestor changed when RIT transitioned to RITmail and we believe that certain elections made when the initial roll-out occurred may have led to this situation.
We are relying on our faithful Quaestor readers to share the following information for any RIT employee that may have missed our last few issues of The Quaestor since RIT switched to RITmail.
- The Quaestor is now distributed to the RIT community via RITmail and is sent to your inboxes from the RIT Newsletter <newsletter@rit.edu> account with the subject “Institute Audit, Compliance and Advisement (IACA) Newsletter - The Quaestor.” Therefore, if you have any rules in your Outlook Inbox moving emails with certain content, these emails may be moved out of your inbox prior to you receiving them.
- The Quaestor email is sent to members subscribed to the category Newsletters in the RIT Communications Center. Click Management Subscriptions to manage your preferences.
Follow these steps to subscribe to The Quaestor!
1. You will need to log in using your RIT User ID and Password.
2. Within the Subscription Center, navigate to the Community Lists page (in Yellow Box below):
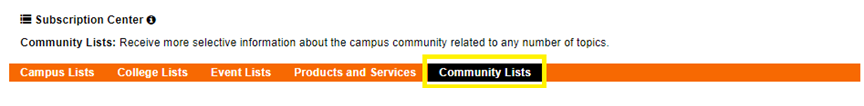
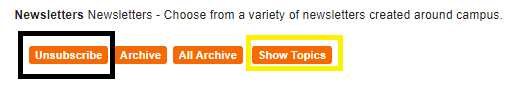
3. Within the Community Lists subscription page, make sure that you are Subscribed to the Newsletters option (in Black Box below – if it says Unsubscribe, it means that you are Subscribed.)
4. Click on the Show Topics button under the Newsletter option (in Yellow Box below).
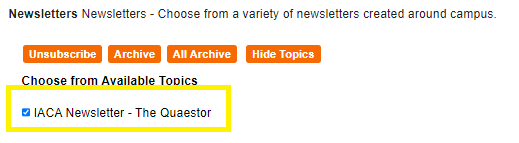
5. Within the Chose from Available Topics – make sure the box next to IACA Newsletter – The Quaestor is checked.
Training Opportunities Provided by IACA
Internal Controls and Fraud in the Workplace
During the 2.5 hour Internal Controls and Fraud in the Workplace class, the importance of, components of, and the responsibility for establishing and maintaining effective internal controls are discussed. Various examples of what can happen when controls are non-existent or break down (i.e., fraud) are shared throughout the class. The session is required in order to receive the RIT Accounting Practices, Procedures and Protocol Certificate of Completion. However, anyone interested in learning about internal controls and fraud prevention is welcome to attend.
To learn more about these important topics, sign up for a session in the RIT Talent Roadmap.
The next training session of Internal Controls & Fraud in the Workplace is: Thursday April 13, 2023, 9:00-11:30 AM - Location: Louise Slaughter Hall, Room 2140
Unit Level Risk Assessment—How to Advance Your Organization’s Agility
The first step towards successfully managing risk is to implement an effective risk assessment methodology. Risk assessment is a systematic process for identifying and evaluating both external and internal events (risks) that could affect the achievement of objectives, positively or negatively. During this 2.5 hour class, we will discuss the key components of an effective risk assessment process and how to integrate it into the business process to provide timely and relevant risk information to management. To learn more about these important topics, sign up for a session in the RIT Talent Roadmap.
The next training session of Unit Level Risk Assessment is: October 18, 2023 from 9:00 - 11:30 AM - Location: Louise Slaughter Hall, Room 2140
Additional Information by IACA
Pop Quiz Challenge: Congrats to Sarah Sarchet, Faculty, NTID Science and Mathematics, our last winner!
Correctly answer the question below to be entered in a drawing to win a prize valued at $15. The winner is chosen randomly and notified by email.
According to Rachel Rohrbaugh, which of the following is NOT a component of a mindful security outlook?
- Gamification
- Looking at the system from the perspective of the opposition
- Carelessness
- Breaking traditional thought patterns
Click here to submit your answer.
Watch IACA’s Monday Minute video series here!
Our video series focuses on opportunities for improving internal controls and increasing awareness of various university processes, policies, and protocols. If you have questions, feel free to contact anyone in the IACA office using information on our webpage. Just to name a few, past topics include: Travel Policy changes, FERPA Regulations, RIT’s Ethics & Compliance Hotline, Records Management Policy, Risk Assessment and many others.
What about ethics in the workplace?
Learn about the RIT Ethics and Compliance Hotline
IACA Team
Learn more about your IACA team.