Quaestor Volume 18, Issue 2
Cybersecurity - Know What You Have
Contributed by: Vernice Stefano, Assistant Director IT Audit, Institute Audit, Compliance and Advisement
When it comes to cybersecurity, the number of Standards, rules, regulations, best practices, minimum practices, etc., that one should follow to safeguard Private or Confidential data, can be overwhelming.
If the approach to cybersecurity can be boiled down to three steps, it would go something like this. . .
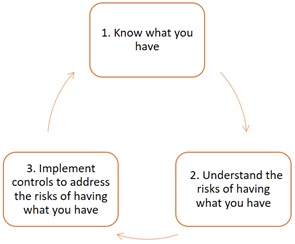
The focus of this article is the first step, Know what you have. Multiple standards and frameworks identify this as a control.
- National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) ID.AM-1: Physical devices and systems within the organization are inventoried.
- Information Systems Audit and Control Association (ISACA)’s Control Objectives for Information and Related Technologies (COBIT) BAI09.01 - Identify and record current assets.
- NIST Special Publication 800-171 (“Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations”): 3.4.1 - Establish and maintain baseline configurations and inventories of organizational information systems (including hardware, software, firmware, and documentation) throughout the respective system development life cycles.
So, how does one proceed? Start by performing an information inventory. RIT’s Information Access and Protection (IAP) Standard 1provides resources to help in this endeavor. Included in the Information Handling Resources link, referred to in the IAP Standard, is the Information Access and Protection Plan Inventory Template 2019 (MS Excel).2 This spreadsheet is a suggested template to aid departments in identifying and maintaining an inventory of all Private, Confidential, and Internal information handled.
Note: RIT has four data classifications. In addition to Private, Confidential, and Internal (i.e., information that “is restricted to RIT faculty, staff, students, alumni, contractors, volunteers, and business associates for the conduct of Institute business,” the fourth classification is Public information (i.e., information that “may be accessed or communicated by anyone without restriction and has no special handling requirements associated with it.”).
Of specific interest, when we perform our reviews, is Tab 4--Applications--Sensitive Data. Tab 4 is a template where you provide a list of the applications that your department uses. Along with this list, the purpose of the application, the application’s vendor, and the different classifications of data are requested. Refer to the following image for a picture of Tab 4.
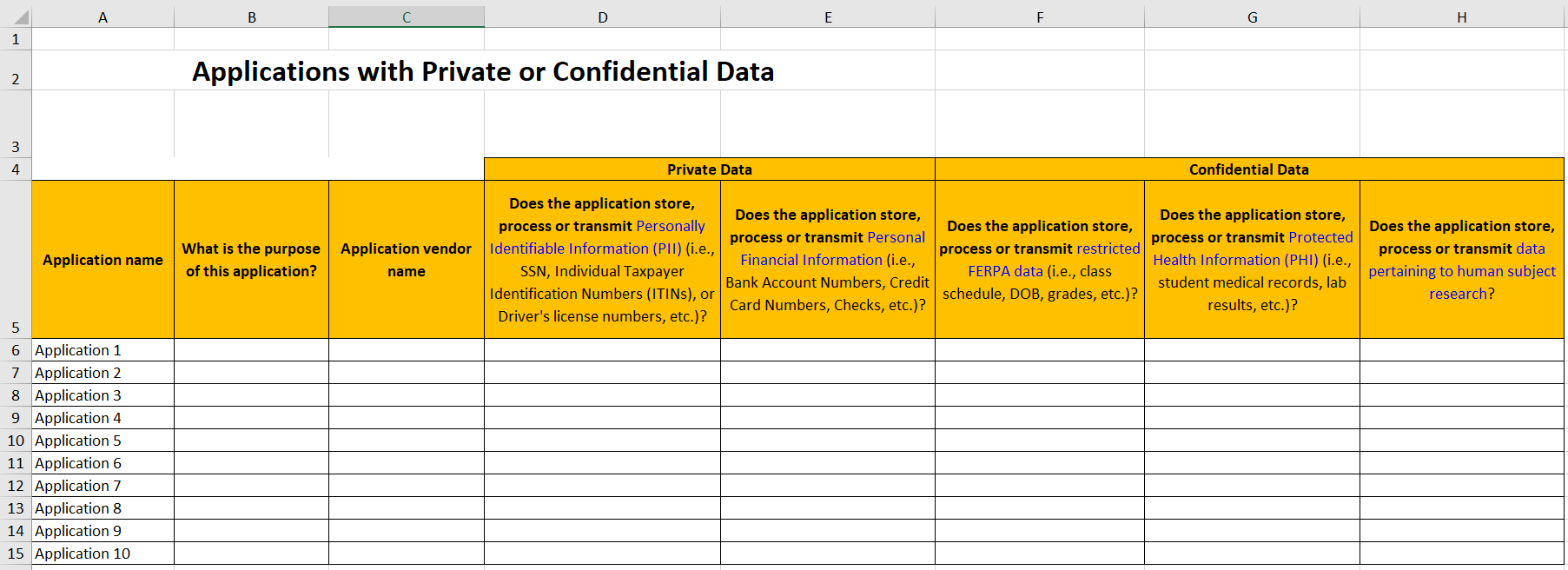
During an audit, however, additional information is requested. These pertain to whether information about European Union (EU) resident data is collected, whether Private or Confidential data is sent to a third party service provider (think cloud service provider), and whether any applications have been retired in the last couple of years.
Why do we ask these additional questions?
The EU resident data question pertains to the EU General Data Protection Regulation (GDPR). Since we have campuses in Croatia (a member of the EU), we want to ensure we are aware of whether we work with RIT Croatia data. Consider whether you work with and exchange data with RIT Croatia. It is important that you know what the classification of that data is.
There are risks and rewards relative to working with cloud service providers/third party service providers. If you use a cloud service provider to store, process, access, or transmit Private or Confidential data, you need to ensure that the provider has the necessary security controls in place and complies with RIT policies and standards, as well as any applicable regulations or applicable industry requirements. The expectation, when Private or Confidential data is involved, is that solution providers have the necessary controls in place. What does that mean for you? If your day-to-day job is not information security, this might be a completely alien concept. But you do play a role. RIT’s Solutions Life Cycle Management (SLCM) Standard3 requires that RIT departments exploring new IT services (including third-party and RIT-hosted, and software as a service) that host or provide access to Private or Confidential information contact the Information Security Office (ISO) and Information and Technology Services (ITS) “prior to investigating, evaluating, selecting, or developing a new solution.” (The ISO would then perform security reviews of the solution to assess the controls at the third party.)
As your needs change or maybe a project or effort is completed, you might find that you no longer need the services of a cloud service provider to process Private or Confidential data. What happens to the data after the relationship ends? Does it get returned to RIT? (Can it be returned?) In what format will data be returned? Actually, these questions should have been raised in the beginning, i.e., during the cloud service provider vetting process.
We have recently added a question on whether any of the applications on the list share data with our enterprise-wide student information system or enterprise reporting platform system, for example. We added this to help us determine whether we need to involve other areas in our review.
If you handle Private or Confidential data, then you are considered to have privileged access. Private data, is defined in RIT’s Information Access and Protection Standard, specifically under Information Classification4, as “information that is confidential and which could be used for identity theft. Private information also has additional requirements associated with its protection (e.g., state and federal mandates).” Confidential data is “information that is restricted to a need-to-know basis and due to legal, contractual, ethical, or other constraints may not be accessed or communicated without specific authorization.”
As a user with privileged access, you are required to take the “RIT Information Handling” training, and you are required to complete this course annually. This training can be obtained via Talent Roadmap (link https://www.rit.edu/talentdevelopment/talent-roadmap). Type in “RIT information handling” to find the course.
Let us know if you have any questions or want to discuss the above further. IACA is always happy to consult and advise departments on cybersecurity and other controls.
References:
1 “Information Access and Protection Standard.” Information Security Office, Policies & Standards, Rochester Institute of Technology, http://www.rit.edu/security/content/information-access-protection-standard
2 “InfoInventory-2019r.xls.” Information Access and Protection Plan, Rochester Institute of Technology, https://www.rit.edu/security/sites/rit.edu.security/files/documents/InfoInventory-2019r.xls
3 “Solutions Life Cycle Management.” Information Security Office, Policies & Standards, Rochester Institute of Technology, https://www.rit.edu/security/solutions-life-cycle-management
4 “Information Handling Resources.” Information Security Office, Requirements, Rochester Institute of Technology, https://www.rit.edu/security/information-handling-resources
MFA Fatigue at RIT
Contributed by: Sophia Larson, Security Communications Associate, Information Security Office
It’s 7:00 AM. You’ve just received a push from Duo to confirm you’re logging into the RIT network. You ignore it, but immediately receive a second push and then a third. You confirm that you’re logging into the network and continue getting ready for work. At 8:30, you start your workday and attempt to login to the network, but your password no longer works. Later that day you find your account quarantined for sending out a job scam message. Now you’re wondering if your data has been compromised.
What just happened? You’ve just become a victim of a Duo fatigue attack. An attacker is repeatedly logging into the RIT network using your username and password. The attacker believes you will eventually accept a push because you’ll think that you must need to login. They may have obtained your password through an authentic-looking phishing email or text.
Multi-Factor Authentication (MFA) is a great tool for keeping accounts secure. However, it does not provide complete protection. Let’s learn a little about MFA to see how it works and how to protect ourselves.
What is Multi-Factor Authentication?
To understand MFA fatigue, you first need to understand what multi-factor authentication is. Multi-Factor Authentication, most commonly referred to as MFA, is a security process that requires individuals to provide multiple authentication factors before gaining access to an online account or system. At its core, MFA is like adding an extra lock to the door of your digital world. The required authentication factors to open this “lock” fall into three categories: something you know, something you have, and something you are.
Something You Know: This will often be something like a password or pin, and is the classic first line of defense that most of us are familiar with.
Something You Have: This will often fall under the physical item category, especially when utilizing Duo MFA. It could be a smartphone, a smart card, or a hardware token. It’s an additional layer of security against attackers, and is especially important because an attacker would need to physically possess this item to gain access.
Something You Are: This typically involves biometric data, such as a fingerprint or facial recognition. It is the most personal and secure form of authentication because it is unique to you.
By combining two or more of these authentication factors, MFA significantly improves security by making it more challenging for unauthorized users to access your accounts, even if they have the password. It provides an extra layer of protection that you should embrace wherever possible; this small step can make a world of difference in safeguarding your digital life.
Duo Security MFA
Multi-factor authentication (MFA) helps ensure the identity and security of our devices when we try to access any systems or data within RIT. By verifying user identity through prompts, Duo MFA helps RIT protect its systems and data by maintaining visibility into authentication events. This happens in addition to submitting a correct password, with prompts often sent to a user's smartphone or other assigned device. At RIT, it is preferred that user’s take advantage of the Duo App. When you log into RIT MyCourses, you get a prompt; when you log into RIT eServices, you get a prompt. Duo MFA has become a frequent interaction in every student, faculty, and staff’s life when accessing RIT information resources. Using Duo MFA is critical to maintaining the integrity of information and data within the RIT community.
MFA Fatigue
While the benefits of MFA are undeniable, there is a growing concern about MFA fatigue. MFA fatigue refers to the weariness or frustration users may experience when encountering MFA prompts during online interactions. If you’ve ever let out a sigh of exasperation when yet another website asks you to click on a Duo notification, you’ve probably felt MFA fatigue! The prompts may feel relentless, and this extra step to maintain integrity may become cumbersome over time, leading to understandable frustration.
Attackers may spam Duo MFA prompts to trick the users into accepting it, out of frustration over pings or even by accident. This is why it is so important to stay vigilant and continue to understand that, the next time you sigh at another Duo prompt, it is a symbol of a safer digital world.
When Should I Expect to Receive a Duo Push?
You should expect to receive a Duo Push, phone call, or text message only when you’re actively at a Duo prompt in a browser. This also includes mini-browsers often used by Outlook, OnBase, VPN, and others. You will tend to see an MFA prompt in any online service that stores or handles private or confidential data, but you also may not receive a push if you have previously logged in since single sign-on (SSO) re-uses a single approved Duo Push across multiple services.
Phone calls and text messages are not the recommended ways to interact with Duo. You should use these methods as a back-up to re-enable your Duo Mobile app should you have the app stop working or if you get a new phone. Having a functioning Duo app future-proofs your Duo experience: it works when there’s no wifi or cellular coverage and can be restored if you have configured backups.
Ensuring that you are utilizing Duo in the recommended way will improve your user experience and reduce issues with the service significantly.
What Should I do if I Receive a Push But I’m Not Logging In?
When incidents happen that involve unexpected MFA prompts, it’s important to remember that you can take steps to remedy it. Be sure to report the incident immediately to the RIT Service Center at help.rit.edu or 585-475-5000 and follow their instructions. To prevent future incidents, be sure to look out for suspicious prompts. These may be in the form of an unusually high number of requests, unrecognized devices sending the prompts, or a push from an unexpected location.
Multi-Factor Authentication is the shield between your digital world and cyber threats. It requires users to provide two or more authentication factors - something they know, have, or are - to access their online accounts, bolstering security in an increasingly interconnected world. Duo MFA, utilized here at RIT, offers a user-friendly approach to MFA and plays a significant role in ensuring the digital security of our community. However, it is essential to acknowledge the concept of MFA fatigue, where users may find the authentication process repetitive and cumbersome. This feeling is understandable, but MFA remains paramount, safeguarding our data, preserving trust, and defending users from ever-evolving cyber threats. So, whether you’re receiving a push notification, entering a pin, or utilizing facial recognition, remember that MFA is your digital fortress, ensuring your online experiences remain secure.
For More Information
Managed Print Services (MPS) move to the RIT Service Center (RSC)
Contributed by: Jennifer Fichtner, Manager, MPS and New Programs, Procurement Services
RIT Managed Print Services (MPS) support is now part of the RIT Service Center (RSC)! RIT partners with Xerox to provide a variety of print/copy/scan devices to the university, while the RSC allows users across campus a central location for self-service options and targeted support.
Many helpful knowledge articles about MPS and printing can be found in the RSC portal. Simply log into the RSC and navigate to the Managed Print Services Knowledge Base:
Or you can simply search for related keywords such as “MPS”, “Xerox”, or “printer”. To make a Service request, simply navigate to the Managed Print Services Catalog:
Or you can find direct links to the service requests on the MPS website.
What does this mean for the university community?
• All requests for Xerox devices including requests for new equipment, replacement equipment, moving a device, or having a device removed will now be submitted through the Self-Service Portal at help.rit.edu.
• Requestors will now have visibility into the status of their request through the entire process and will receive real time updates.
• Xerox, Procurement, and ITS will now be able to more efficiently track and manage the installation and removal process.
• RIT will now have the ability to track metrics regarding the number of requests and response times to help drive additional process improvements.
• Requests for service of Xerox devices or ordering supplies will not transition to the RSC. Departments will still make these requests by calling Xerox Support directly at 855-474-6358. Xerox’s on-site support technician will continue to support RIT in the same manner as before.
• Colleges/Departments that are not supported by ITS will now use the RSC to submit their requests. Xerox will work directly with the appropriate IT support personnel to complete the ticket.
Procurement Services will be monitoring the effectiveness of the new process to ensure that clients are not impacted by this change. We welcome your feedback!
Training Opportunities Provided by IACA
Internal Controls and Fraud in the Workplace
During the 2.5 hour Internal Controls and Fraud in the Workplace class, the importance of, components of, and the responsibility for establishing and maintaining effective internal controls are discussed. Various examples of what can happen when controls are non-existent or break down (i.e., fraud) are shared throughout the class. The session is required in order to receive the RIT Accounting Practices, Procedures and Protocol Certificate of Completion. However, anyone interested in learning about internal controls and fraud prevention is welcome to attend.
To learn more about these important topics, sign up for a session in the RIT Talent Roadmap.
The next training sessions of Internal Controls & Fraud in the Workplace are:
- Tuesday November 14, 2023, 9:00 AM - 11:30 AM - Location: Louise Slaughter Hall, Room 2140
- Wednesday January 10, 2024, 1:00 PM - 3:30 PM - Location: Louise Slaughter Hall, Room 2140
- Tuesday February 6, 2024, 1:00 PM - 3:30 PM - Location: Virtually via Zoom
- Thursday April 11, 2024, 9:00 AM - 11:30 AM - Location: Louise Slaughter Hall, Room 2140
- Thursday July 18, 2024, 1:00 PM - 3:30 PM - Location: Louise Slaughter Hall, Room 2140
Unit Level Risk Assessment—How to Advance Your Organization’s Agility
The first step towards successfully managing risk is to implement an effective risk assessment methodology. Risk assessment is a systematic process for identifying and evaluating both external and internal events (risks) that could affect the achievement of objectives, positively or negatively. During this 2.5 hour class, we will discuss the key components of an effective risk assessment process and how to integrate it into the business process to provide timely and relevant risk information to management. To learn more about these important topics, sign up for a session in the RIT Talent Roadmap.
Additional Information by IACA
Pop Quiz Challenge: Congrats to Jennifer McKean, Senior Financial Assistant, College of Art and Design, our last winner!
Correctly answer the question below to be entered in a drawing to win a prize valued at $15. The winner is chosen randomly and notified by email.
According to Vernice Stefano, RIT's Information Access and Protection (IAP) Standard provides resources to what?
- Help departments understand revenue recognition
- Establish Individual Conflict of Interest and Commitment management plans
- Aid departments in identifying and maintaining an inventory of all Private, Confidential, and Internal information in their possession.
- Guide purchasing of equipment over $9,999
Click here to submit your answer.
Watch IACA’s Monday Minute video series here!
Our video series focuses on opportunities for improving internal controls and increasing awareness of various university processes, policies, and protocols. If you have questions, feel free to contact anyone in the IACA office using information on our webpage. Just to name a few, past topics include: Travel Policy changes, FERPA Regulations, RIT’s Ethics & Compliance Hotline, Records Management Policy, Risk Assessment and many others.
What about ethics in the workplace?
Learn about the RIT Ethics and Compliance Hotline
IACA Team
Learn more about your IACA team.