Quaestor Volume 19, Issue 1
Three Lines Model - Risk Management and IACA’ s Role
Contributed by: Neeraj Sama, Senior Internal Auditor, Institute Audit, Compliance and Advisement
Educational institutions, such as RIT, need to adopt a comprehensive approach to risk management to systematically mitigate the risks involved in emerging issues and challenges. To have an effective risk management framework, institutions must implement a dynamic governance structure and processes that help maintain a strong internal control environment and achieve set business objectives.
IIA’s Three Lines Model
The “Three Lines Model,” published by the Institute of Internal Auditors (IIA) in 2020, replacing the old “Three Lines of Defense Model,” is a structured principle-based framework that provides an aid to organizations to manage their risk environment and enhance governance effectively.
According to the principles of the Three Lines Model (see below), the governance of an organization should have appropriate structure and processes to ensure that the governing body is accountable to stakeholders for organizational oversight, the organization’s management manages risk and takes actions toward the achievement of business objectives, and internal auditors provide independent assurance and facilitate continuous improvement in the operations.
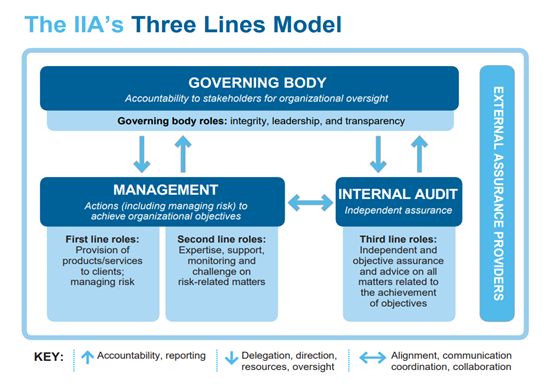
RIT’s governance framework as presented below conforms to the principles of IIA’s ‘Three Lines Model’:
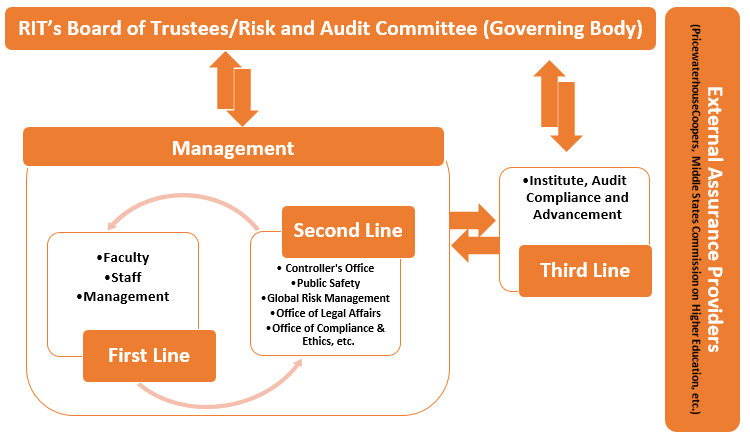 RIT’s Board of Trustees and its sub-committees (Governing Body) oversee the overall governance through leadership and management and are accountable to its stakeholders (i.e., students, donors, research sponsors, employees, etc.).
RIT’s Board of Trustees and its sub-committees (Governing Body) oversee the overall governance through leadership and management and are accountable to its stakeholders (i.e., students, donors, research sponsors, employees, etc.). - RIT’s first-line management roles are responsible for running the operations and service delivery to its stakeholders while managing the inherent operational risks by implementing mitigating controls.
- RIT’s second-line management roles are compliance and risk management experts and support first-line management.
- RIT’s third-line role is Institute Audit, Compliance, and Compliance (IACA). The auditors work with first and second-line management roles, report to the governing body, and provide confidence and objective and independent assurance to the governing body about the adequacy of implemented internal controls and the effectiveness of governance while recommending continuous improvements.
- RIT’s external auditors and accreditation agencies provide additional assurance regarding financial reporting and quality of education to protect the interest of stakeholders.
IACA’s Role in Risk Management as a Third-Line
Risk management is an integral part of RIT’s operations, performed at all levels. However, as a third line, IACA plays an important role in risk management activities at RIT by providing auditing and management advisory services. IACA maintains its independence and objectiveness through its reporting structure and functionally reports to the Risk and Audit Committee (i.e., a sub-committee of the RIT’s Board of Trustees and a Governing Body) while administratively reporting through Finance and Administration. As part of its audit and advisory services, IACA evaluates the adequacy and effectiveness of implemented internal controls and identifies and assesses potential risks that may negatively impact RIT’s operations, finances, or reputation. IACA provides recommendations to mitigate the identified risks but it is the responsibility of first-line management to mitigate these risks, after considering the cost vs. benefit of implementing new or modifying existing controls.
As part of their audit services, IACA evaluates whether RIT departments comply with applicable laws and regulations and identifies opportunities to further mitigate non-compliance risk. IACA also participates in RIT’s overall enterprise risk management activities at an oversight level and considers the university-level risks while finalizing its annual audit plan. Other services provided by IACA include:
- The continuous monitoring of RIT’s internal control environment through continuous audits, identification of non-compliance with RIT’s policies, and making suggestions for improvements to the control environment.
- Providing unbiased and value-added advisory services and ongoing support to RIT management in implementing process and system changes and navigating challenges.
- Providing training on topics including Internal Controls and Fraud in the Workplace and Unit Level Risk Assessment through the RIT Talent Roadmap.
IACA supports RIT’s business objectives in its day-to-day affairs and is always open to suggestions to help improve its operations.
Reference
- The IIA’s Three Lines Model: An update of the Three Lines of Defense, The Institute of Internal Auditors, September 2020
GoogleGroups Phishing - What You Need To Know
Jarred King, RIT Student Employee reporting to Ben Woelk, Governance, Awareness, & Training Manager, Information Security Office (ISO)
You received an email that you have a new message in your GoogleGroups inbox. The information seems important, but you don’t remember joining the group. You’re suspicious but decide to check it out anyway to see what the message says. You might be wondering, Is GoogleGroups Phishing Me?
Let’s find out more about this new phishing attempt to see how it works and how we can protect ourselves.
Threat actors have upped their game and are using legitimate, reputable domains to send phishing emails in their newest attempt to steal your personal information.
You may receive harmless email notifications from GoogleGroups notifying you that you have a new message. The message contents are often a scam! This style of phishing can often bypass traditional spam filters through the use of trusted reputable domains like Google.
What is GoogleGroups?
GoogleGroups is an online bulletin and communication space for teams, departments, or support groups to host forum-like discussions. Think about Reddit; GoogleGroups is very similar to this, but all members of a group are notified, by email, anytime there is new information posted in the group.
Additionally, GoogleGroups allows others to automatically add you to a group without permission. While you might receive notification you have been added to a group, this is not an invitation that you can accept or deny – you are just automatically added to the group.
GoogleGroups Phishing Example:
Your GoogleGroups inbox looks very similar to your email inbox. Each record represents a group that you are a member of:
As a member of a group, messages like these are common:
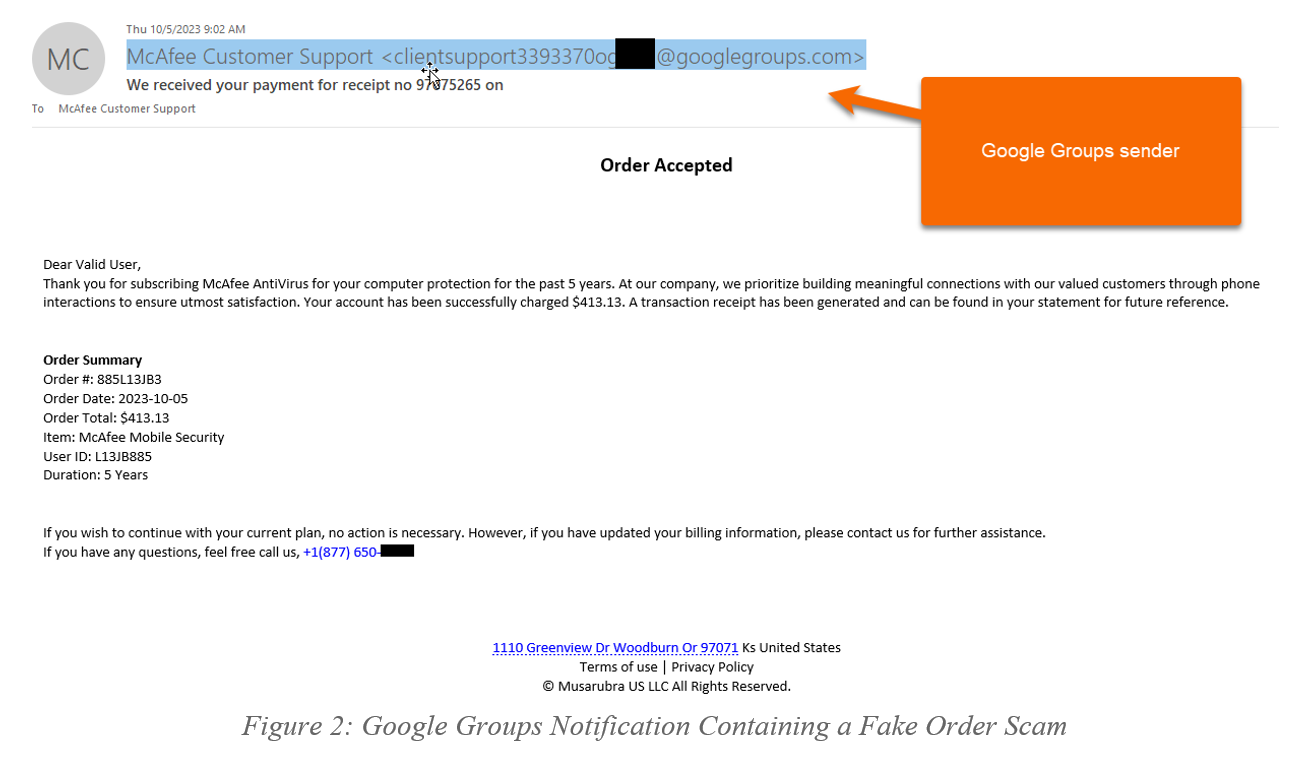
This email bypassess spam filters through the use of the @googlegroups domain. However, it shares similar red flags to other email scams that can help you identify this as phishing.
- The sender appears as McAfee Customer Support but it is from @googlegroups.com. Businesses will always use their own domain (like @mcafee, etc.) to contact their customers.
- This email is addressed to “Dear Valid User”: businesses will address customers by name if the order is real. Vague communications are often scams.
- The message indicates you have been automatically charged. This creates a sense of urgency to ensure you can receive a “refund.” Urgency is often associated with phishing attempts.
This GoogleGroups example under McAfee Customer Support is just one instance of this type of phishing. Always be on the lookout for these red flags and anything else that looks suspicious.
How Can I Protect Myself?
To decrease the risk of this scam happening to you, you can update the settings in your GoogleGroups account to limit external and unsolicited actions in GoogleGroups.
You can update your global settings by going to https://groups.google.com and clicking on -> ‘Global Settings’ By unchecking ‘Add me to their groups’ in the Global Settings menu you can ensure that you will not be added to any unexpected groups in the future. Ensure ‘Invite me to their groups’ is checked so groups must invite you to join. Be sure to ‘Save’ your settings after modifying them.
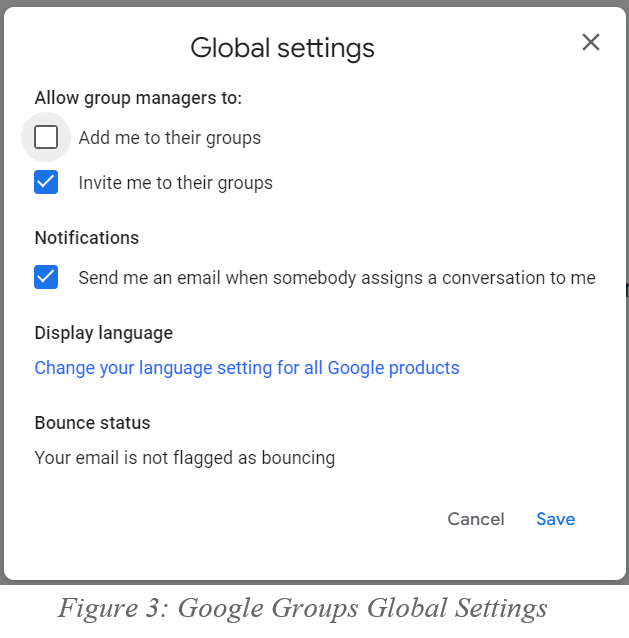
In the future, if you are being invited to a group that you are not aware of, it is probably a scam. Ignore or deny any unexpected GoogleGroups notifications/messages and report them to RIT.
Reporting Phishing:
Anyone can be a victim of a scam, be cautious and remain vigilant when interacting with electronic content. Remember to report anything you feel may be suspicious to spam@rit.edu with the phishing attempt attached.
Also check out the RIT phish bowl to familiarize yourself with up-to-date information on attacks observed in the RIT community.
For More Information
RIT Operation Tiger Cloud: Ready to Work[day]
Contributed by: Theresa Steward, Executive Director, Technology & Process Excellence, Technology Management, Controller's Office
RIT's enterprise resource planning (ERP) system, known as Oracle EBS, myInfo/myBiz, or eBiz, has served the institution since 1998 and is near the end of its service life. Although Oracle continues to deliver compliance and security-related patches, new functionality and modern enhancements have dwindled. In response, RIT kicked off Operation Tiger Cloud to initiate a competitive selection process for a replacement system, ultimately selecting Workday as the preferred solution to manage the finance, human resources, payroll, and budget functions.
The current focus of the Operation Tiger Cloud project is to identify a System Implementation (SI) partner, a standard practice when deploying a modern cloud ERP. This partner will play a pivotal role in shepherding the University through the technical and functional complexities of the project. The team has also engaged with other higher education institutions that have already migrated to Workday, drawing valuable insights as RIT seeks the optimal partnership for our institution.
The Operation Tiger Cloud project is set to gain momentum in the coming months with a planned go-live date in early 2026 for financials, payroll and human resources, followed by the implementation of the budget module. However, the go-live is just the starting point. The true transformative potential lies in how we, collectively, leverage the system to enhance efficiency and redirect our focus to value-added activities. Imagine a shift from labor-intensive data handling to the actual analysis of information!
The RIT community will have numerous opportunities to engage in the project, participating in activities such as user testing, informal labs, ad hoc feedback sessions, and formal training initiatives. The central hub for communication is the Operation Tiger Cloud project website, supplemented by additional channels to support the project's organizational change management strategy. Currently, the website features pre-implementation details, including project announcements and FAQs. However, as we progress, you can expect updates on milestones achieved, calls to action, testimonials, and information on training opportunities.
We want to connect with you and invite you to participate in the engagement opportunities that will be forthcoming. The Operation Tiger Cloud team will be providing an update at upcoming Staff Council and Faculty Senate meetings and we encourage you to take advantage of those opportunities to learn more about the project. We also want to engage with the RIT community through a variety of options including features available on the website for you to submit questions, comments, or ideas. While these types of projects are commonly referred to as "system" implementations, Operation Tiger Cloud is fundamentally driven by and designed for people. Your input is invaluable, and we cannot wait to connect with you as we collectively embark on this transformational journey!
Training Opportunities Provided by IACA
Internal Controls and Fraud in the Workplace
During the 2.5 hour Internal Controls and Fraud in the Workplace class, the importance of, components of, and the responsibility for establishing and maintaining effective internal controls are discussed. Various examples of what can happen when controls are non-existent or break down (i.e., fraud) are shared throughout the class. The session is required in order to receive the RIT Accounting Practices, Procedures and Protocol Certificate of Completion. However, anyone interested in learning about internal controls and fraud prevention is welcome to attend.
To learn more about these important topics, sign up for a session in the RIT Talent Roadmap.
The next training sessions of Internal Controls & Fraud in the Workplace are:
- Tuesday April 30, 2024, 9:00 AM - 11:30 AM - Location: Louise Slaughter Hall, Room 2140
- Thursday July 18, 2024, 1:00 PM - 3:30 PM - Location: Louise Slaughter Hall, Room 2140
Unit Level Risk Assessment—How to Advance Your Organization’s Agility
The first step towards successfully managing risk is to implement an effective risk assessment methodology. Risk assessment is a systematic process for identifying and evaluating both external and internal events (risks) that could affect the achievement of objectives, positively or negatively. During this 2.5 hour class, we will discuss the key components of an effective risk assessment process and how to integrate it into the business process to provide timely and relevant risk information to management.
The next training sessions of Unit Level Risk Assessment are:
- Wednesday March 27, 2024, 9:00 AM - 11:30 AM - Location: Louise Slaughter Hall, Room 2140
- Wednesday October 23, 2024, 1:00 PM - 3:30 PM - Location: Louise Slaughter Hall, Room 2140
To learn more about these important topics, sign up for a session in the RIT Talent Roadmap.
Additional Information by IACA
Pop Quiz Challenge: Congrats to Amanda Dolan, Senior Staff Specialist, School of Life Sciences, our last winner!
Correctly answer the question below to be entered in a drawing to win a prize valued at $15. The winner is chosen randomly and notified by email.
Which of the following is NOT included in the First Line of RIT's governance framework?
- Staff
- Management
- Faculty
- Controller's Office
Click here to submit your answer.
Watch IACA’s Monday Minute video series here!
Our video series focuses on opportunities for improving internal controls and increasing awareness of various university processes, policies, and protocols. If you have questions, feel free to contact anyone in the IACA office using information on our webpage. Just to name a few, past topics include: Travel Policy changes, FERPA Regulations, RIT’s Ethics & Compliance Hotline, Records Management Policy, Risk Assessment and many others.
What about ethics in the workplace?
Learn about the RIT Ethics and Compliance Hotline
IACA Team
Learn more about your IACA team.