Business Email Compromise (BEC)
- RIT/
- Security/
- Resources/
- Types of Threats/
- Business Email Compromise (BEC)
Recognize, Respond, Report
Business email compromise (BEC) is a type of spear phishing scam where the attacker impersonates or compromises an executive’s email account to manipulate the target into unknowingly disclosing sensitive information. These attacks most commonly target individuals with purchasing or other fiduciary responsibilities or regularly handle sensitive information within an organization.
Recognize
- The attacker will often pose as an executive-level employee.
- Typically, attackers use urgency to receive compliance, if the email requests you to immediately initiate a wire transfer or purchase, this is a red flag.
- Verify the sender address is legitimate and not a slight variation (For example,. samkellyrit@gmail.com vs. sam.kelly@rit.edu)
- If the email requests a wire transfer that coincides with the travel of a trusted employee, this is often a BEC.
Respond
- Verify all unexpected requests by calling or meeting with the person.
- Carefully check the sender's address and context and tone of the email.
- Report spam and phishing emails to spam@rit.edu
Report
- If you believe you may have been victimized by a BEC, contact the RIT Service Center by phone at 585-475-5000, or online at help.rit.edu to open an incident report.
What is RIT doing to protect me?
- Rejecting emails from known spammers and malicious websites.
- Ensuring email is coming from the server it claims to be from.
- Implementing traditional anti-malware and anti-spam protection.
- Quarantining suspicious messages sent via email.
- Restricting the ability of others to send from RIT email addresses belonging to high-profile individuals.
How do BEC scams work?
- BEC scams often start with a phishing email intended to obtain unauthorized access to a targeted employee's account.
- The attacker may exchange a series of emails with the targeted employee in order to build a trusted relationship. Even though these emails do not normally contain links or attachments, they still pose a risk by connecting the attacker to internal sources.
- Scammers can pretend to be trusted vendors or employees inquiring about payments or sensitive data.
- Scammers will email employees from embedded contact lists or even call them, earning their trust.
- When the targeted employee is out of reach, such as away on business, the cyber thief could send a fake email from his or her office demanding that a payment be made to the trusted vendor's account.
- With no way to verify if the email is authentic, the employee may make a hasty decision to approve the payment. Of course, the payment goes to the scammer and not the trusted vendor.
Correcting Outlook Autofill
After replying to a BEC attempt, the fraudulent address is now cached in Outlook and may be auto-filled the next time you try to send to the legitimate sender.
For those who have replied to a BEC attempt, this is how to correct the problem with Outlook autofill.

You receive a seemingly harmless email. Your boss is asking for some help. They usually don't email you from their personal account, but this seems pretty urgent and you know they are out of the office today. To be helpful you respond right away by simply saying you can help.
Thankfully after some time, you realize this was too fishy and report the BEC attempt to spam@rit.edu. Done, right? No. The fake email will still be at the top of your autofill address bar.
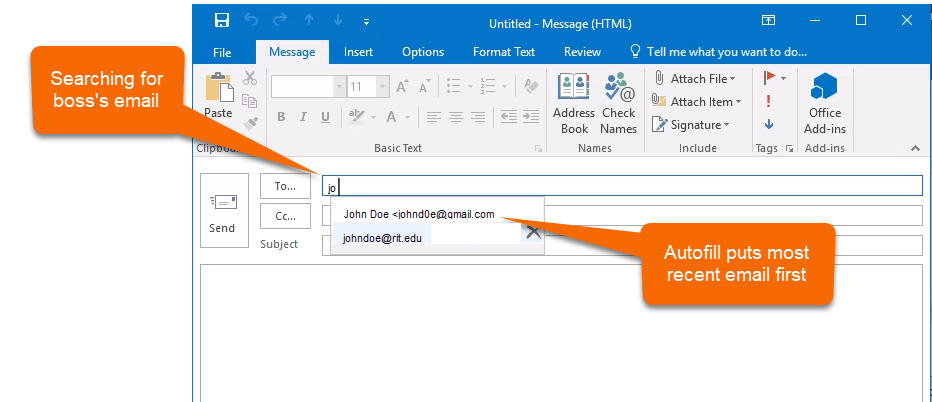
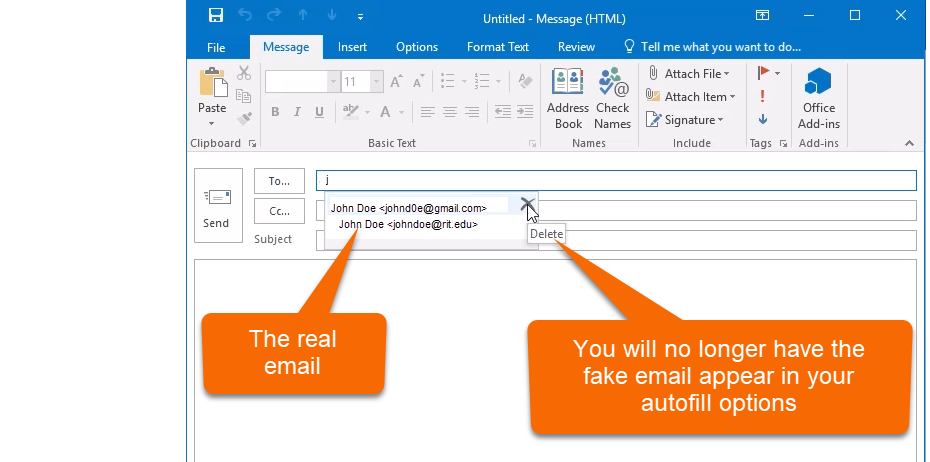
Here is how to make sure the next email you send to your boss doesn't go to the attacker. Delete the email from your autofill options.
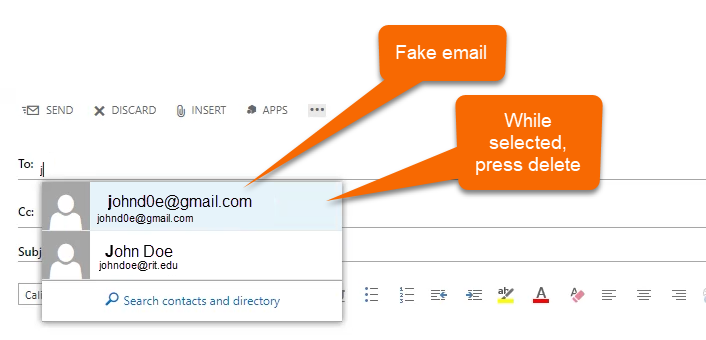
For those that use the Outlook Web App, while selecting the fake email, press the delete button on your keyboard.
For More Information
- FBI - Business E-Mail Compromise (external)
- TrendMicro - Business Email Compromise (external)
