Cybersecurity and Research at RIT: Regulatory Compliance
What is CMMC?
Research at RIT is subject to various compliance requirements. One example of compliance requirements is the Cyber Maturity Model Certification (CMMC). CMMC can be understood as the verification mechanism the US government uses to audit contractors’ compliance to NIST SP 800-171 and NIST SP 800-172.The Department of Defense (DoD) created CMMC in response to the continued exfiltration of Controlled Unclassified Information (CUI) from its supply chain. The Cybersecurity Maturity Model Certification (CMMC) ensures the appropriate cybersecurity controls and processes are implemented to protect Controlled Unclassified Information (CUI).
DoD contractors and researchers need to obtain certification that meets requirements for the CMMC maturity level appropriate to the work they wish to do for the DoD. The new CMMC mandate includes university-based research labs and facilities—as well as FFDRCs (Federally Funded Research and Development Centers) and UARCs (University Affiliated Research Centers). This means RIT researchers are not exempted if they want to work with the Department of Defense (DoD).
According to the National Archives, CUI is information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls.
When RIT researchers have a government contract or award that indicates that they are working with CUI, or contract clauses that indicate that NIST SP 800-171 or NIST SP 800-172 controls are required, they will be required to work within CUI research computing environment to ensure the confidentiality, integrity, and availability, of the CUI data is secured.
RIT is focused on creating and maintaining the appropriate cybersecurity maturity level which would assist our researchers who are required to protect CUI data.
CMMC Program Goals
- Safeguard sensitive information
- Enforce Defense Industrial Base (DIB) cybersecurity standards
- Ensure Accountability while minimizing barriers to compliance
- Perpetuate a collaborative culture for cybersecurity and cyber resilience
- Maintain public trust through high professional and ethical standards
CMMC 2.0 Model
The CMMC 2.0 model streamlines program goals/requirements to three cybersecurity levels and aligns each level's requirements to widely known and accepted NIST cybersecurity standards. When receiving a contract with the DoD you may be required to meet one of the following levels as a condition of contract.
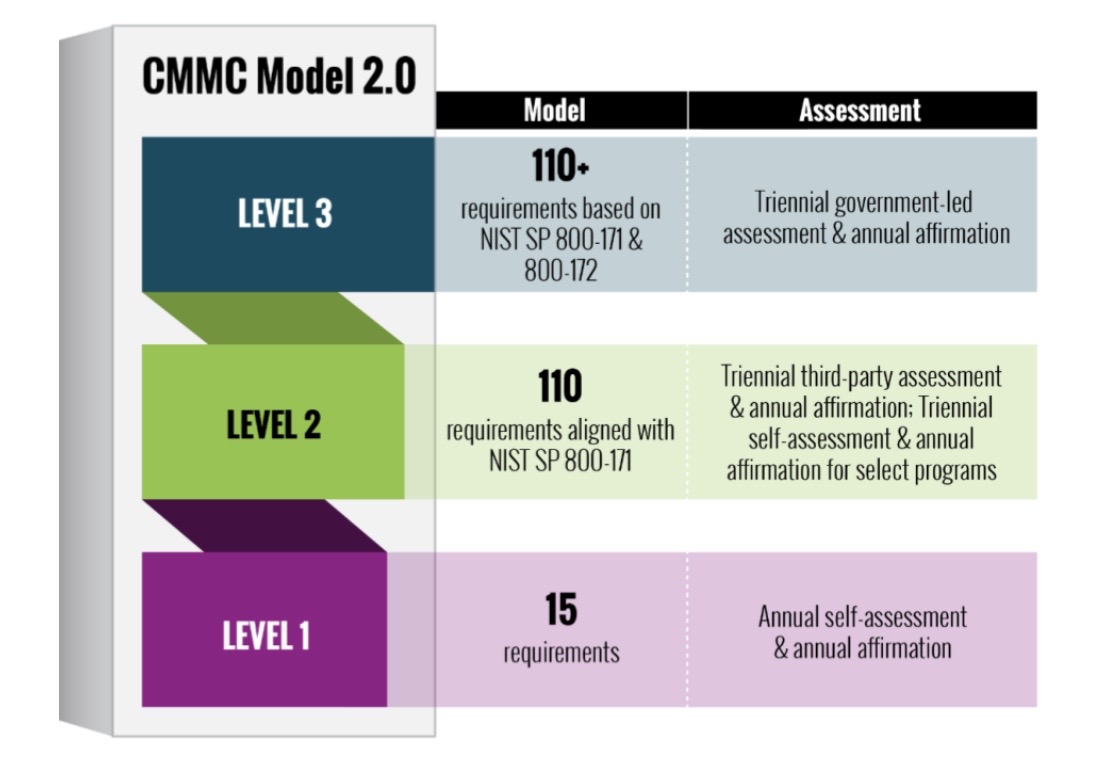
The graphic above indicates the CMMC 2.0 model; its levels and assessment types for each. The key takeaway of CMMC 2.0 is that it is more restrictive than CMMC 1.0. Some activities that previously would require only self-assessment may now require third-party assessment to remain compliant.
Some Best Practices for Securing CUI Under CMMC
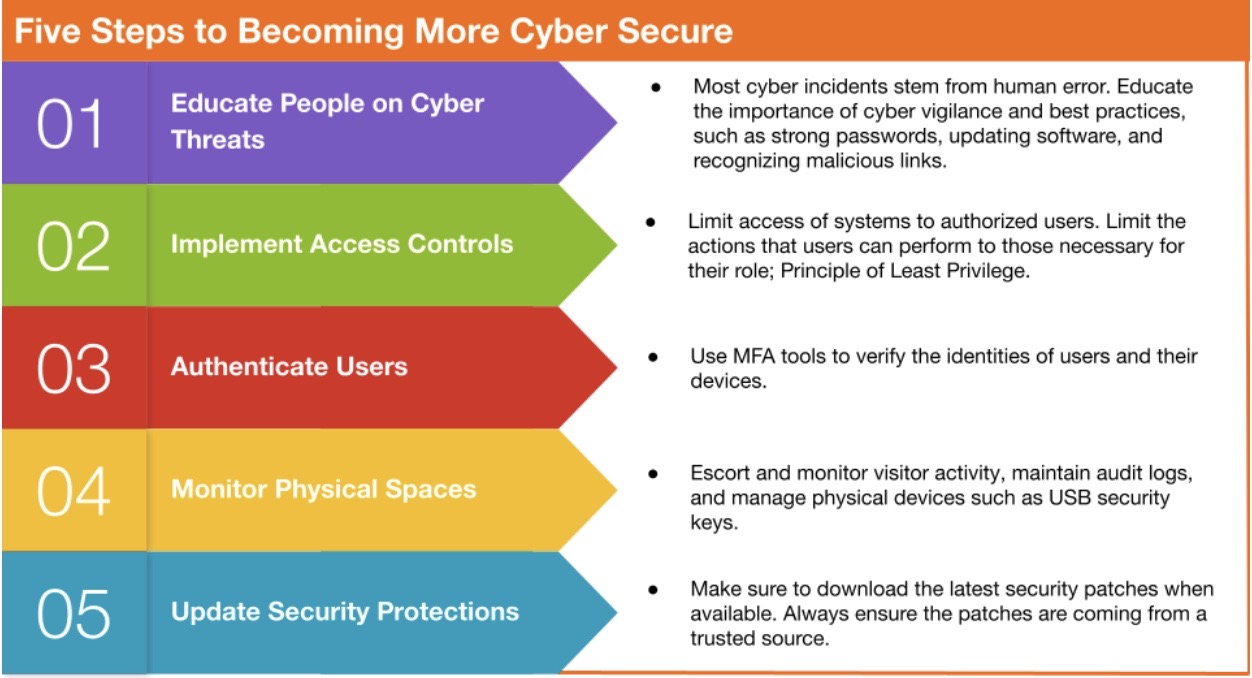
For more information and resources to help you protect research data and comply with cybersecurity requirements in grants, contracts, and data use agreements, contact:
- Sponsored Research Services
- Office of Compliance and Research
- Research Computing
- Information Security Office (Email: infosec@rit.edu)


