V2V Security Course
We are pleased to offer the instructional and lab materials on this page to the community — for free — as the foundation for a 3-4 week training course on connected vehicle security.
Disclaimer: Any opinions, findings, and conclusions or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the National Security Agency.
Hands-on Lab Activities

Lab 1 - Introduction to V2V (PDF)
How to set up an experimental environment for studying V2V security using our open-source software-defined radio testbed, V2Verifier. Configure and install V2Verifier, and run simple experiments. Estimated completion time: 60-75 minutes.
Lab 2 - BSM Spoofing Attack (PDF)
Learn about BSM spoofing, a straightforward but dangerous attack against V2V communications. Configure and execute a BSM spoofing attack using V2Verifier, then enable IEEE 1609.2 security to observe the importance of security mechanisms like digital message signing and verification for V2V. Estimated completion time: 45-60 minutes.
Lab 3 - BSM Replay Attack (PDF)
Investigate another serious type of attack against V2V communications, the BSM replay attack. Use the testbed to experiment with executing a BSM replay attack, then enable IEEE 1609.2 security and learn how that standard's mitigation mechanisms are designed to prevent this type of attack from being effective. Estimated completion time: 45-60 minutes.
Lab 4 - Cellular Vehicle-to-Everything (C-V2X) (PDF)
Dig into the details of C-V2X, an expanding V2V technology based on cellular LTE and 5G technologies. Take a close look at the physical and MAC layers of LTE-based C-V2X to learn its advantages over other generations of V2V protocols, and examine how security is (and is not) built into C-V2X standards. Optionally, study how commercial C-V2X implementations build on basic C-V2X standards with application-layer security and data exchange protocols. Estimated completion time: 60-75 minutes (75-90 minutes with optional activity).
Lecture Slides
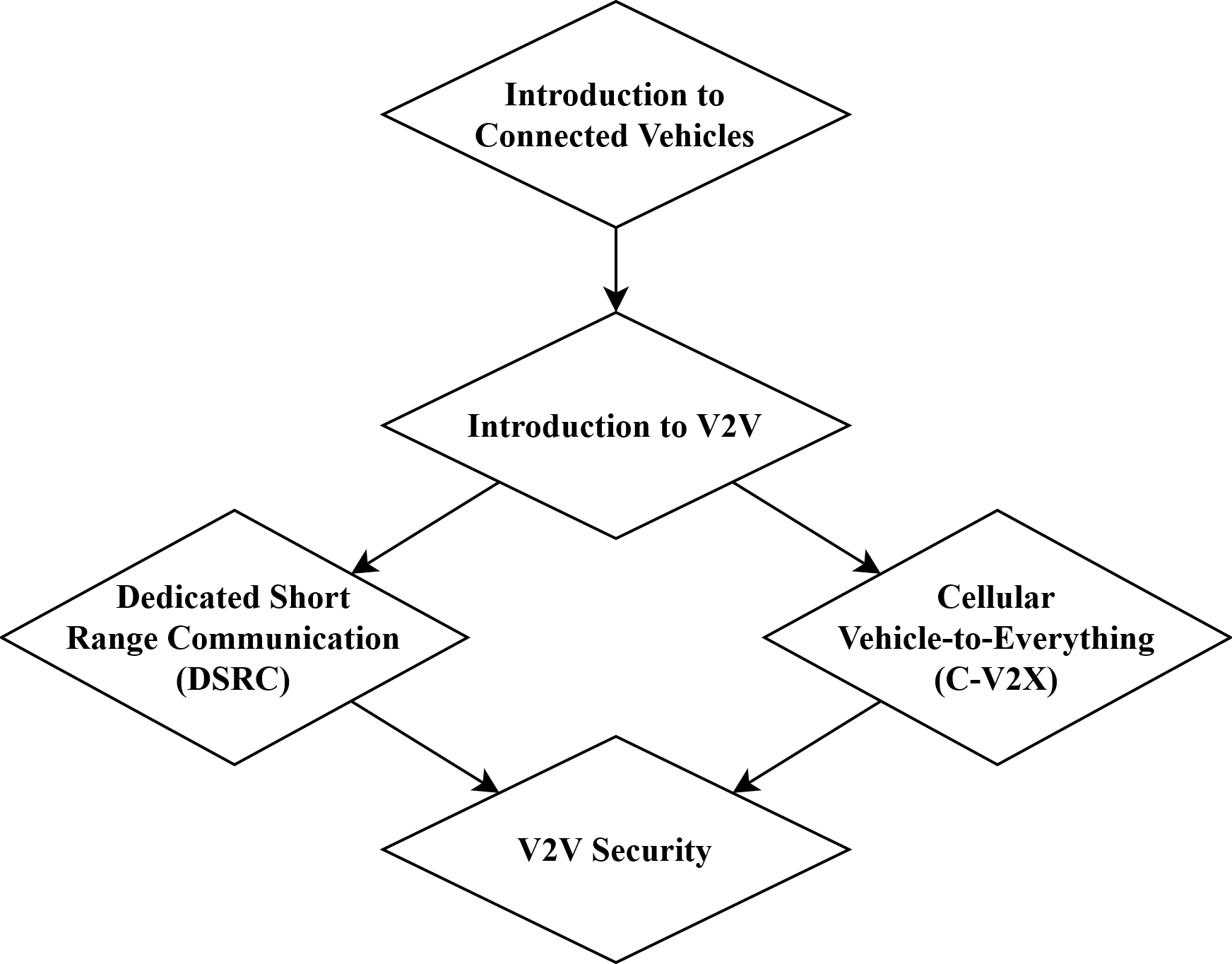
- Introduction to Connected Vehicles (CVs) - a brief overview of CV history, technologies, regulation and global deployments.
- Introduction to V2V Communication - V2V applications, technical challenges of developing V2V technology, how V2V can improve roadway safety, security challenges in V2V.
- V2V Technologies Part 1 - Dedicated Short Range Communications - the DSRC protocol from physical to application layer, including the benefits, limitations, and future directions of this first-generation V2V technology.
- V2V Technologies Part 2 - Cellular Vehicle-to-Everything - a comprehensive look at LTE- and 5G-based C-V2X protocols from physical to application layer.
- V2V Security - V2V security requirements, limitations and vulnerabilities of current V2V protocols, security improvements in next-generation V2V protocols, the IEEE 1609.2 standard for V2V security, and V2V security infrastructure.
Additional instructional resource: a summary of V2V Simulators and Related Software
V2Verifier Testbed
V2Verifer is an open-source software-defined radio (SDR) testbed for studying security problems in vehicle-to-vehicle (V2V) communications. V2Verifier features the first open-source implementation of the IEEE 1609.2 standard for V2V security, with features including V2V message signing and verification as well as privacy-preserving pseudonymous identification. Support is also included for WAVE Short Message Protocol (WSMP) based on the IEEE 1609.3 standard. At the lower communication layers, V2Verifier supports both major V2V protocols, Dedicated Short Range Communication (DSRC) and Cellular Vehicle-to-Everything (C-V2X).
Related Publications
Geoff Twardokus and Hanif Rahbari, "Evaluating V2V Security on an SDR Testbed," IEEE International Workshop on Computer and Networking Experimental Research using Testbeds (CNERT) in conjunction with IEEE INFOCOM 2021, Virtual Conference, May 2021. [ pdf ]
Videos
Quick Demo: V2Verifier Configuration
V2Verifier can be used in a wide variety of experimental scenarios, including non-line-of-sight (NLOS) evaluations as shown here.
Quick Demo: V2Verifier Mobility
V2Verifier's use of software-defined radios (SDRs) allows us to evaluate mobile scenarios; for example, we can place devices on mobile carts (as shown here) or even in moving vehicles for real-world evaluation.
Evaluating V2V Security on an SDR Testbed
An introduction to V2Verifier, our software-defined radio (SDR) testbed for secure vehicle-to-vehicle (V2V) communication. We describe the motivation and architecture of V2Verifier, demonstrate how V2Verifier can be used to experiment with attacks against V2V protocols, and show how V2V security standards (IEEE 1609.2) can effectively mitigate certain types of attacks against V2V. This presentation was originally given at the Computer and Networking Experimental Research using Testbeds (CNERT) workshop held in conjunction with IEEE INFOCOM 2021.
Targeted Discreditation Attack Against Trust Management in Connected Vehicles
This video describes how our vehicle-to-vehicle (V2V) security testbed, V2Verifier, can be used to identify security flaws in V2V technology. We briefly introduce V2Verifier, then we introduce and experimentally validate a novel reactive jamming attack against a major V2V protocol. This presentation was originally given at IEEE ICC 2021. Discussion of V2Verifier and demos using the testbed begin at 7:58.
Resources and Further Reading
- Qualcomm - Cellular Vehicle-to-Everything
- Qualcomm - 5G NR-based C-V2X
- Qualcomm - How NR-V2X Supports Advanced V2X Use Cases (Apr 2020) (PDF)
- Qualcomm - C-V2X Evolution for Advanced Use Cases (Aug 2019) (PDF)
- Qualcomm - C-V2X Trial in Japan Results (Dec 2018) (PDF)
- Rohde & Schwarz - Wireless Communications for Automotive Applications (2021 White Paper) (PDF)
- 5GAA - V2X Benchmarking Report (Sept 2018) (PDF)
- U.S. Dept. of Transportation - The Safety Band (5.9 GHz RF)
- U.S. Dept. of Transportation - Interactive Connected Vehicle Deployment Map




