New IEEE standard will significantly improve performance in switched data center networks
RIT researchers invent Meshed Tree loop-avoidance protocol, creating a new industry standard
A team of RIT computing researchers created Meshed Tree Bridging protocol, a new standard for loop-avoidance that will make large data center networks faster and more reliable.
Computing researchers at Rochester Institute of Technology have developed a new loop-avoidance protocol that solves a key challenge faced in switched networks, including many of the data center networks that run our internet and cloud services.
The new protocol is an improvement on current loop-avoidance solutions, as it significantly increases how fast and reliably computer networks can recover from failures. The protocol, called Meshed Tree Bridging protocol, has extremely low convergence time on detection of link or network component failure — and all without needing complex solutions.
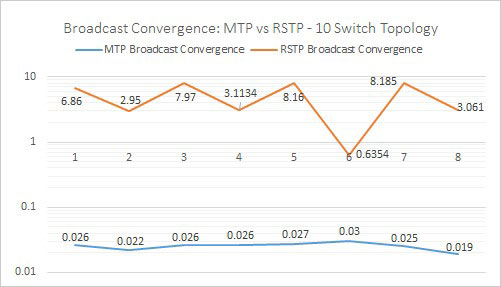
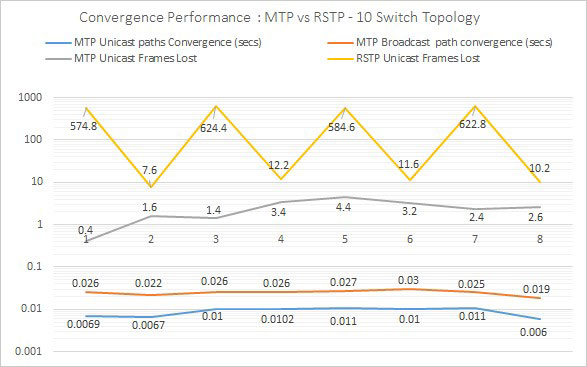
In this convergence latency performance comparison, Meshed Tree protocol took milliseconds to converge, while Rapid Spanning Tree protocol took several seconds.
Meshed Tree Bridging with Loop Free Forwarding has been accepted as an IEEE working standard — meaning industry can now begin adopting the technology created at RIT.
“Meshed Tree Bridging protocol is capable of addressing the data forwarding needs of the large data center networks that play a significant role in our everyday computing activities, without requiring complex and highly redundant infrastructure,” said Nirmala Shenoy, professor in RIT’s School of Information, who led the team. “We are making our protocol code available and want to work with industry to tune and upgrade the specifications, in order to see the solution deployed.”
The original looping of frames problem stems from a component in computer networks called a switch, which is used to direct data from a source device to a destination. When a switch or link fails, these data frames can become trapped in an endless loop and never arrive at the final destination.
For decades, Rapid Spanning Tree (RST) protocol has been commonly used for loop-avoidance. However, it can cause temporary network outages that are detrimental to network performance and services. Newer loop-avoidance protocols were introduced, but they are complex and require costly infrastructure.
Compared to the outdated Rapid Spanning Tree protocol, Meshed Tree protocol lost significantly fewer data frames during single link failure.
“The RST protocol has high convergence times during certain topology changes, resulting in unacceptably high latencies,” said Shenoy. “This is especially true with root switch failure, because the root switch is the foundation of a spanning tree topology.”
To better solve the loop-avoidance and failure problems, the RIT team took a new approach. They invented a new Meshed Tree algorithm, which they used to develop their protocol.
The algorithm allows switches to store a bundle of paths. This means that when failure is detected on the main path, failover to a backup path is immediate. The Meshed Tree algorithm can also use knowledge of the switch ports in use and the structure of the meshed trees to detect attempts to modify or interfere with the topology.
The team studied simulations and prototypes of their protocol in various network topologies, in order to compare it to RST protocol. The protocol code was evaluated using the Global Environment for Network Innovation (GENI) testbeds. The experimental results showed that Meshed Tree protocol has very high recovery speeds and resiliency to network component failures.
Studies found that in identical test cases, Meshed Tree protocol networks take milliseconds to converge, while RST protocol took several seconds. When comparing the number of data frames lost during single link failures, RST protocol lost up to 600 frames, while Meshed Tree protocol lost fewer than five frames.
To make the protocol official, the team navigated the standards-making process at the Institute of Electrical and Electronics Engineers (IEEE), a professional association that develops, defines and reviews technology standards. More than 50 distinguished IEEE members examined the protocol in a global peer-review process, before it was finally accepted as an official IEEE standard.
“Nirmala and the RIT team are applying rigorous academic research methods to determine if the Meshed Tree Bridging protocol is superior to the existing ones,” said James Moore, vice-chair of the Technical Activities Board Committee on Standards and IEEE member. “With a demonstration of its merits, they may be able to attract the industrial participation that would be vital to the uptake of the standard.”
“We also hope that Nirmala and the team’s efforts provide an example that demonstrates to other researchers that applying their disciplines to standards will result, not only in academic ‘credit,’ but will hasten the progress of good ideas to industry implementation via the standardization process,” added Moore.
Meshed Tree Bridging protocol was created by Shenoy; Bruce Hartpence, professor in the School of Information; Bill Stackpole, professor in the Department of Computing Security; and Daryl Johnson, associate professor in the Department of Computing Security. Peter Willis, a computing and information sciences Ph.D. student in RIT’s Golisano College of Computing and Information Sciences, also contributed to the project and is continuing the work as part of his dissertation.
RIT researchers see large data centers as key beneficiaries of Meshed Tree protocol. These data centers can contain hundreds of servers that might handle search and web lookup traffic. The predominant research focus in data center networks is currently on robust architectures to strengthen failure resiliency and use multiple protocols to address discovery of shortest paths and load balancing.
“Fast algorithms and protocols are crucial to cutting down reconfiguration latency and improving failure resiliency in these data center networks,” said Shenoy. “Our Meshed Tree algorithm and protocol can address these challenges, without excessively overloading the networks with multiple protocols, specifically for tree-based data center network architectures.”
In the future, the RIT team will focus on including cybersecurity options as part of the protocol.
“The idea that security is included in the protocol is not true of many competing standards, including spanning tree,” said Hartpence. “Often a vendor will implement a feature that adds security, but it is not part of the running protocol itself.”
For more information about Mesh Tree Bridging Protocol, go to the IEEE website.
Related Story